Lately I’ve been using quite a lot the FTP over HTTP protocol in Forefront TMG 2010 SP1(Update 1).
The main reasons for this are:
- malware inspection can be applied to FTP traffic.
- URL filtering can be applied to FTP traffic.
Note that although there are some advantages, also there are some limitations of FTP over HTTP, see the Extra Notes below.
Normally the malware inspection and the URL filtering apply just for HTTP and HTTPS traffic.
For example say a I create an access rule like:
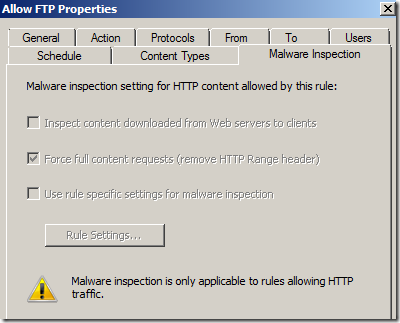
If we take a look on the Malware Inspection settings(right-click the rule and click Properties) of this rule, we can see the option Inspect content downloaded from Web servers to clients to enable malware inspection for it is grayed out:
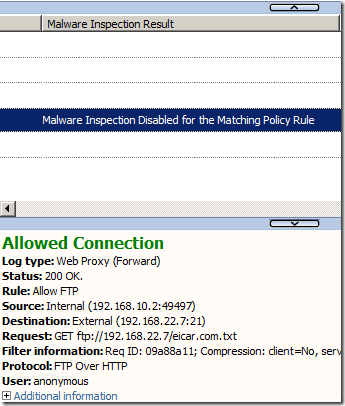
The logs on TMG tell us that malware inspection is disabled for this rule:
If we add the HTTP protocol to the above rule(no need to apply the configuration on TMG yet):
And then look again of the Malware Inspection settings(right-click the rule and click Properties) of this rule, now we will see the option Inspect content downloaded from Web servers to clients to enable malware inspection for this rule available:
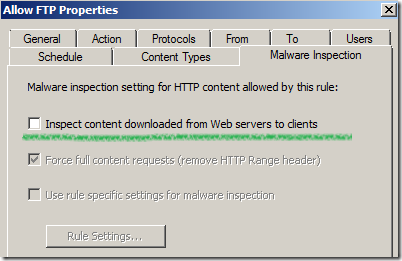
Check the Inspect content downloaded from Web servers to clients check box, click OK to close the rule’s Properties window, remove the HTTP protocol from the rule; then apply the configuration on TMG.
After doing all these, looking at the Malware Inspection settings of this rule we will notice that this time Inspect content downloaded from Web servers to clients check box is checked and grayed out:
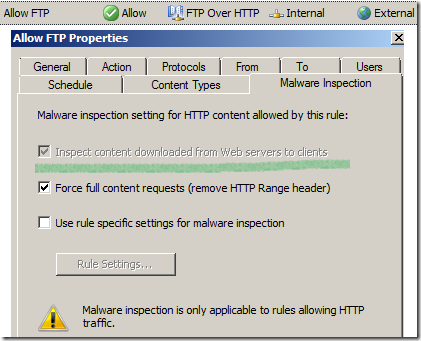
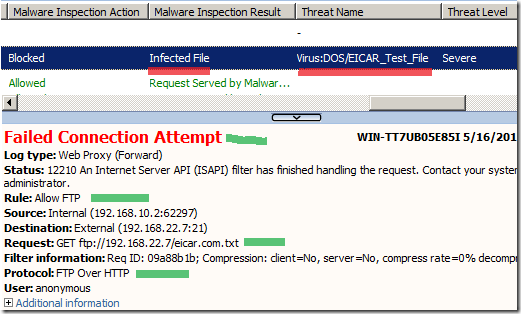
We can then test if indeed the malware inspection will detect malware served by FTP servers.
Below I’m going to put the Eicar virus test file on a FTP server and try to download this file from a client behind TMG.
As can be noted, indeed it works:
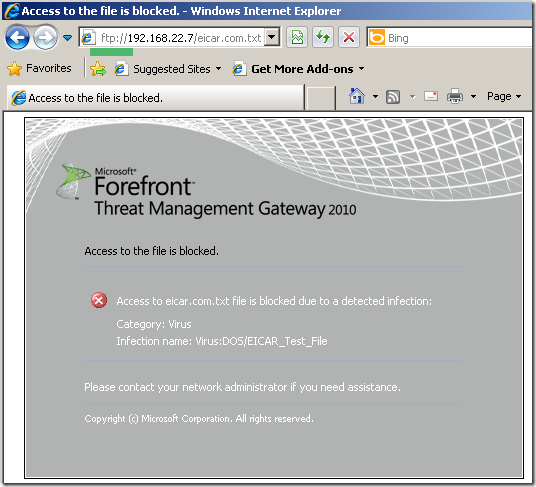
To use the URL filtering with FTP over HTTP, on the above rule I will remove the External network from the Destination(To tab on the Properties window of the rule) and add an allowed URL category, for example Technical Information.
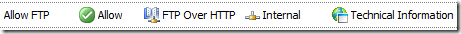
When I attempt to access an allowed FTP destination, as expected, my request will be allowed:
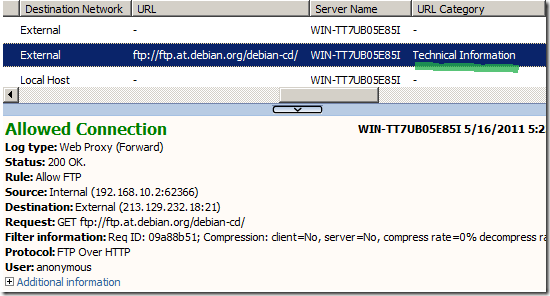
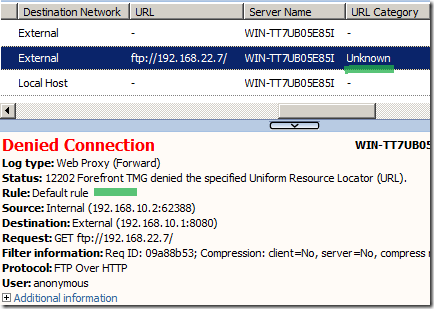
And when the requested FTP destination falls outside of the Technical Information category, the request will be denied:
Extra notes for the FTP over HTTP protocol
- by default, uses Active dode mode although Microsoft’s docs [1][2] seem to say it uses Passive mode(I did not enable Active Mode on TMG's FTP filter as described in [3] or so); I can confirm that the HKEY_LOCAL_MACHINE/SYSTEM/CurrentControlSet/Services/W3Proxy/Parameters/NonPassiveFTPTransfer registry entry set to 0 enables FTP passive mode for the FTP over HTTP protocol.
- you cannot use FTP upload from a Web Proxy client, only FTP downloads are supported. [1]
- to access FTP sites that require authentication, credentials should be specified in the address bar using the following format: ftp://username:password@FTP_Server_Name [1]
- limited to clients which support FTP over HTTP, like IE; other popular FTP clients like FileZilla(as writing) will not work.
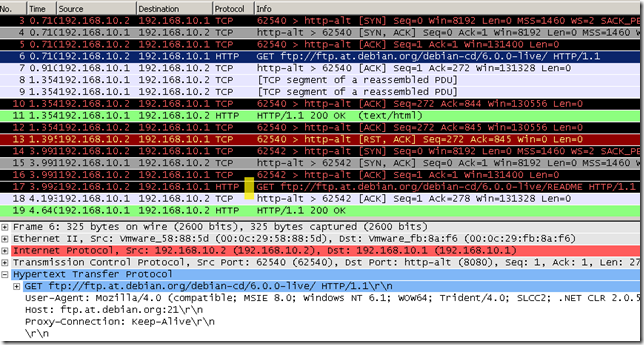
How FTP over HTTP works
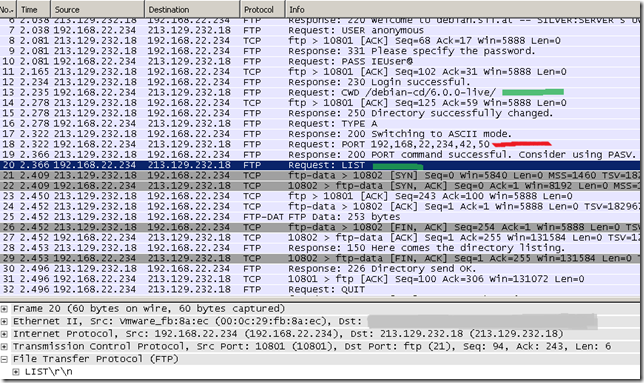
In a short explanation, the web proxy client(IE in this example) connects to the web proxy on port 8080, and issues a GET command for the desired ftp://neededlink URL. Basically below, TMG will see this request, act as a FTP client and will issue a LIST command to the FTP server to list the needed directory, and after it gets the answer from the FTP server will present it to the FTP client within an HTTP 200 OK message.
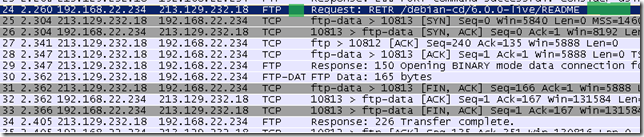
The requested below example file is retrieved by TMG from the FTP server with the RETR command.
References
[1] Forefront TMG 2010 Unsupported configurations/Protocol and Application issues/FTP limitations for Web Proxy clients
http://technet.microsoft.com/en-us/library/ee796231.aspx#t4t4e4t
[2] How to enable passive CERN FTP connections through ISA Server 2000, 2004, or 2006
http://support.microsoft.com/kb/300641
[3] Error 502 “Active FTP not Allowed” when trying to list files in a FTP session behind Forefront TMG 2010
http://blogs.technet.com/b/yuridiogenes/archive/2010/03/16/error-502-active-ftp-not-allowed-when-trying-to-list-files-in-a-ftp-session-behind-forefront-tmg-2010.aspx