|
24.06.2008
ISA Server 2006 as an L2TP/IPsec VPN server and Mac OS X 10.4.x as L2TP/IPsec VPN clients - Part 2: IKE Authentication with Pre-shared Keys
- 1. Configure the ISA L2TP/IPsec VPN server
- 2. Configure the Mac OS X L2TP/IPsec VPN client
- 3. Test the VPN connection
- 4. Miscellaneous
In the first part, we've discussed about using certificate for IKE authentication.
Let's talk now about using pre-shared keys.
Pre-shared keys are a weak authentication method, but they can be useful for testing.
As we have seen, using certificate for IKE authentication can cause some problems.
Having some NAT devices along the path or connecting while we are behind a restrictive firewall can introduce certain issues too.
Pre-shared keys allow us to take a step by step approach in configuring our L2TP/IPsec VPN connections.
For example, we can configure ISA and the Mac L2TP/IPsec VPN clients to use a pre-shared key for IKE authentication, then make a first test while there is no other device(especially a NAT device which might break our connection) between the Macs and ISA. If this test is successful, we know that the second level of authentication (user authentication) is working too. After that we can make a test while the Mac is behind a NAT device(to see if NAT-T is working or if the NAT device is not breaking the NAT-T process).
If this test is successful, we can proceed and configure ISA and the Mac L2TP/IPsec VPN clients to use certificates for IKE authentication, then make a first test while there is no other device(especially a NAT device) between the Macs and ISA. And so on ...
It was a simple process to configure Mac OS X 10.4.8 or Mac OS X 10.4.10 to use pre-shared keys with L2TP/IPsec.
I did not encounter any problems.
1. Configure the ISA L2TP/IPsec VPN server
The authentication methods enabled on ISA are shown in Figure64. I've configured a pre-shared key on ISA.
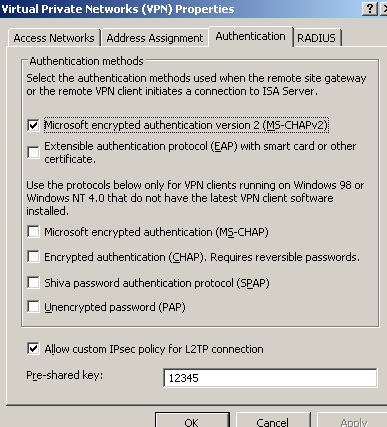
Figure64: ISA - VPN Authentication Methods
2. Configure the Mac OS X L2TP/IPsec VPN client
On the Mac machines, my user has admin privileges, see Figure65.
Figure65: User Adrian
Launch the Internet Connect application, see Figure66.
Figure66: Applications - Internet Connect
And click the VPN padlock or from the File menu, click New VPN Connection.
Select L2TP over IPSec.
And click Edit Configurations.
I've configured this VPN connection, see Figure67. I've entered the pre-shared key in the Machine Authentication - Shared Secret box.
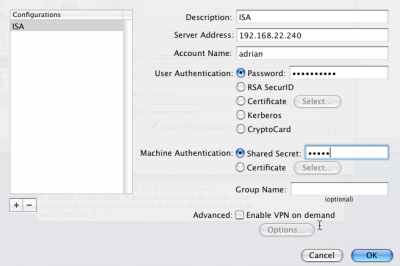
Figure67: VPN(L2TP) - ISA
I've entered in the Server Address field the IP address of ISA.
You can enter the FQDN of ISA if you want. To be able to test without having a DNS server available to resolve the FQDN isabranch.carbowind.net, I've added the needed entry in the /etc/hosts on the Mac, see Figure68.
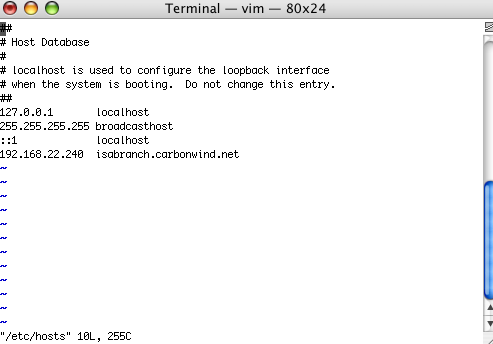
Figure68: etc/hosts
3. Test the VPN connection
And like in part 1, before initiating the VPN connection, from the menu I've selected Connect and clicked Options, see Figure69. As can be noted I've checked the Use verbose logging checkbox. Also there are a couple of important settings there too. Split tunneling is disabled, the Send all traffic over VPN connection checkbox is selected.
Another checkbox, Disconnect when user logs out is selected too. On a Windows XP machine, there is a registry setting, so the VPN session is disconected when a user logs out if the user let it connected. If I modify this registry entry, when the user logs out, the VPN session is not terminated, thus when another users logs in, this user can use the existing VPN connection to access resources on the corporate network. I've made a quick test on the Mac, I've unchecked the Disconnect when user logs out and Disconnect when switching user accounts checkboxes, initiated the VPN connection and succesfully connected, logged out, and logged in with a different user. And I could use the existing VPN connection to access resources on the corporate network.
So, if your Mac is a multi-user machine, keep an eye on these settings.
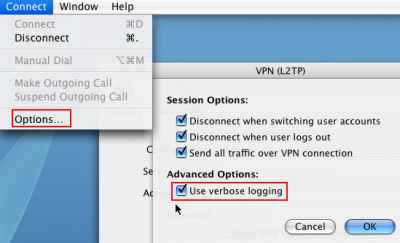
Figure69: Use verbose logging
Hit the Connect button.
And we are connected and we have connectivity, see Figure70(connected by specifying ISA's IP address in the Server address box), Figure71(connected by specifying ISA's FQDN address in the Server address), and Figure72.
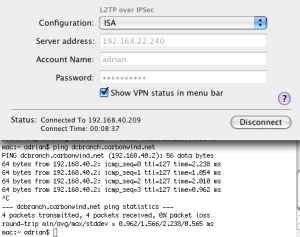
Figure70: VPN (L2TP) ISA Successfully Connected
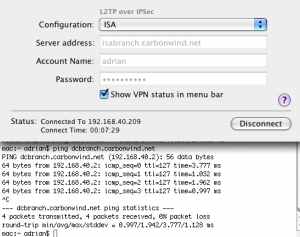
Figure71: VPN (L2TP) ISA Successfully Connected
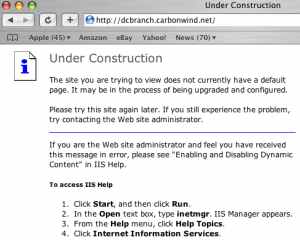
Figure72: Access a Web Site
4. Miscellaneous
It appears that the tested Mac OS X 10.4.8/10.4.10 have an option to export the VPN configuration, see Figure73.
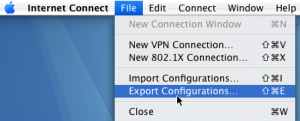
Figure73: Access a Web Site
I did not have the chance to test that, to see what settings are exported(the user's password, the pre-shared key if we use pre-shared keys, if this pre-shared key is exported, it is exported in clear or encrypted ...).
This option, if it works, can be useful if you have multiple Mac machines because it can simplify management. You can create a working configuration on a Mac, export it, and then import it on the other Mac machines.
Also as can be noted from Figure67, the tested Mac OS X 10.4.8/10.4.10 seem to support EAP-TLS for user authentication (we can select a user certificate).
I did not have the time to test this either.
As said before, if I will have the chance to test these features or to test with a Mac OS X 10.5.x I will try to add another part letting you know what I will manage to do.
|