Doing a Forefront TMG 2010 deployment, I went to test if the malware inspection was working.
First thing to do was to access the eicar.org site for the standard Eicar virus test; as expected TMG blocked the request.
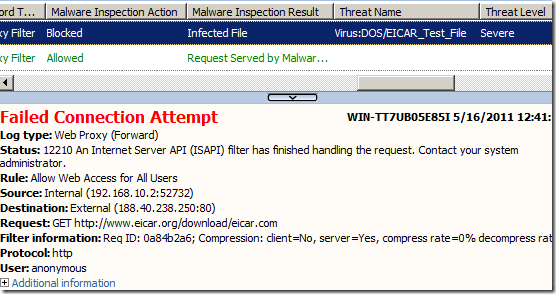
To be honest it’s been a while since I did not click through TMG the Eicar zip archives links on the mentioned site.
As far as I remember(and searching through my blog entries I found an old one related to a beta version of TMG [3]), TMG used to block access to those archives; maybe I have this impression from the beta stages or so, not sure.
Now, when I clicked an archive link, I could actually download the zip file.
Surprised a little, I’ve taken a look at TMG’s logs:
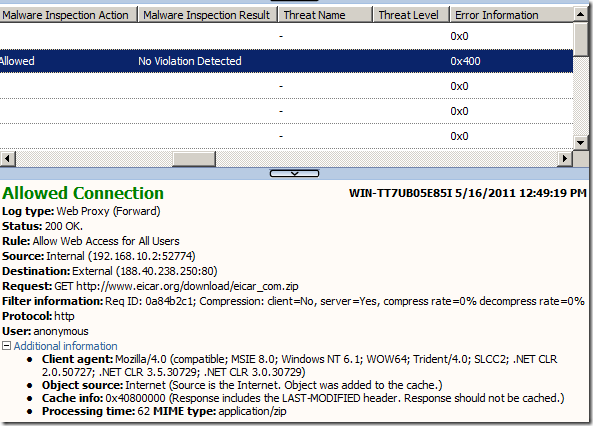
The malware inspection related logs did not seem to show anything specific; the Error Information log field also does not seem to show anything either. [1][2]
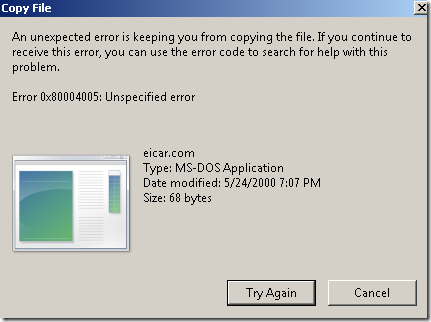
Attempting to extract the downloaded archive on the client side(Windows 2008 R2 server) using the Windows’ zip utility, I could not; seems the archive was corrupted or so, see the below error:
Opening with a hex editor the original file:
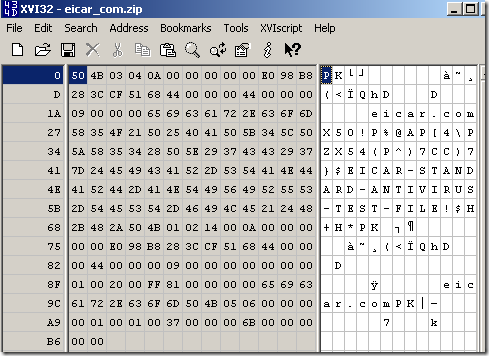
And the file downloaded through TMG:
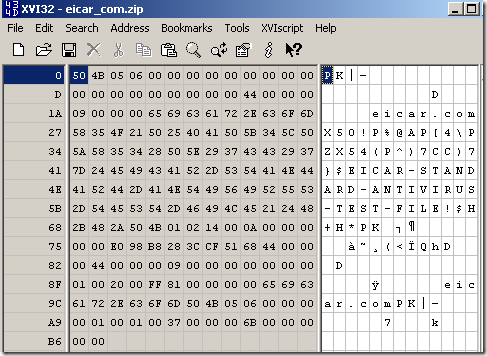
Could be seen that the downloaded one was altered, note its headers.
I kinda had an idea what TMG malware inspection setting might have caused this, the Attempt to clean files that are found to be infected one(checked by default [4]):
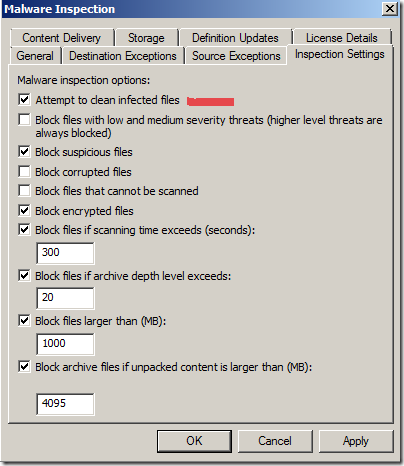
Unchecked this option and tested again; now as expected TMG blocked the file download(I think Error Information code 0x580=400+100+80 or so [1][2]):
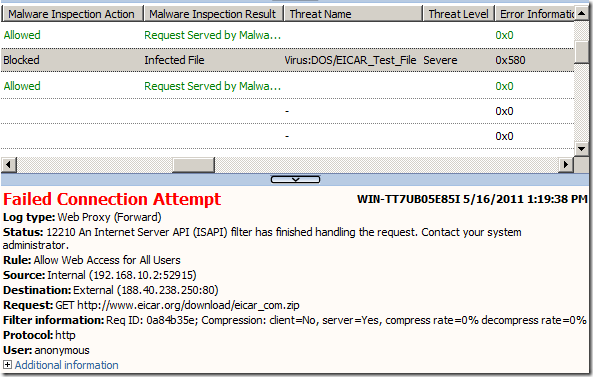
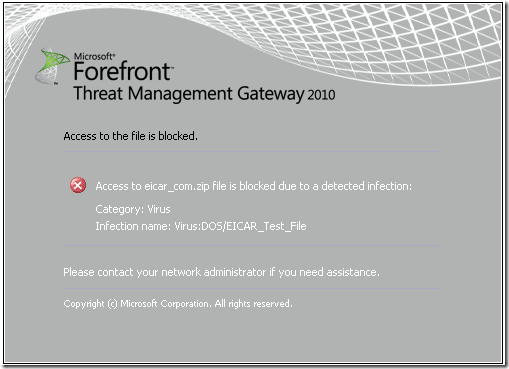
Not sure why this is not done anymore, however, during TMG’s beta days, I remember the logs mentioning when a file was “cleaned” by the malware inspection(Malware Inspection Action log field) and the threat name indicated(Threat Name log field). [5]
Now since apparently the zip file was attempted to be “cleaned” by the malware inspection and the logs did not indicate this, things were a little bit confusing.
References
[1] Web proxy error log values
http://technet.microsoft.com/en-us/library/cc441745.aspx
[2] Web proxy log fields
http://msdn.microsoft.com/en-us/library/dd447850.aspx
[3] TMG Beta 2 – Quickly Print Screening Through
http://www.carbonwind.net/blog/post/TMG-Beta-2-e28093-Quickly-Print-Screening-Through.aspx
[4] Overview of malware inspection
http://technet.microsoft.com/en-us/library/dd182018.aspx
[5] Exercising TMG Beta 2 NIS with PoC
http://www.carbonwind.net/blog/post/Exercising-TMG-Beta-2-NIS-with-PoC.aspx