- With great power comes great responsibility.
- All too often arrogance accompanies strength, and we must never assume that justice is on the side of the strong. The use of power must always be accompanied by moral choice.
There was some heated debate on Twitter the last 24 hours regarding the StartSSL security breach [1].
Apparently all started with a tweet from Ivan Ristic:

Ivan’s (legit) request seems to have attracted a sort of an unexpected reaction from Eddy Nigg.
Instead of diplomatically straight things up he looks set to engage in an argue with everybody.
I won’t post below all Eddy Nigg’s tweets(they are still all on his Twitter profile [2]).
Instead I will post only the relevant parts where I think Eddy Nigg is wrong.
Attack or breach seem to be one and the same thing to Nigg whatsoever:
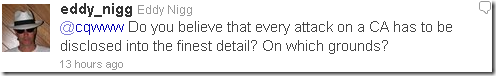
I beg to differ, not all attacks = breach; if it was a breach disclosure is needed and according to the statement posted on the StartSSL site it was a breach.
He says he has “FULL trust of any concerned party”:
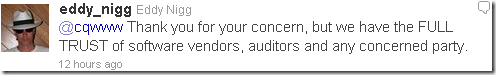
This is not true, as long as his CA(s) are trusted by browsers or vendors for certain operations automatically on behalf on their users; every user using those browsers or apps from those vendors is a concerned party.
The problem of this trust is that simple users cannot act and ask for removal of his CAs from the trusted roots to show their true current level of trust. The way vendors establish to trust a root CA for various operations varies per vendor and end users have little influence on how the decision is made.
For example Apple says: [3]
”Apple will accept your root certificate as it deems appropriate in its own discretion.”
For the average user it is virtually impossible to manually manage these trusted root CAs; I’m sure Nigg is fully aware about this so he must treat with more diplomacy and transparency the end users.
An interesting reply from Ivan Ristic “you’ve just lost a customer”, others follow:
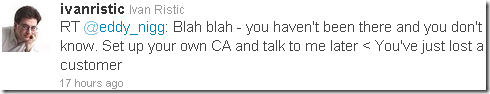
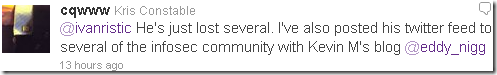
For the reasons mentioned above, Eddie Nigg still have Ivan and the rest as customers; in fact he gets new customers every time users install a browser or so which trust his root CA(s).
Nigg has no use of his certs if nobody trusts them; it’s still unclear to me as writing who are “any concerned party” in his definition. Perhaps another tweet of him reflects this, a reply to another Ivan Ristic’s tweet:

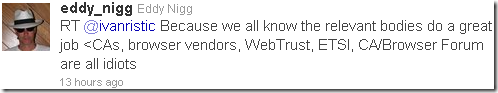
So what’s all about these relevant bodies?
Basically these bodies influence a couple of things; for the moment, just like in the financial industry the CAs benefit of certain “freedom”.
Nigg makes a couple of references to these throughout his tweets:
- particularly he isn’t force to disclose to public what happened during a security breach; he may decide if to do that or not and if yes at what extent.
- he can also decide on what basis to temporally cease the operations of some CA services during a breach without providing much explanation to the public. Note that some institutions may have the power to force him to cease the operations of the CA services in certain cases; according to Nigg’s tweet this time he decided that.
- legally he’s covered and he does seem to take full advantage of that.

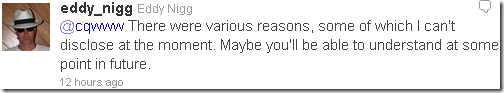
Nigg talks about name and shame opportunities:
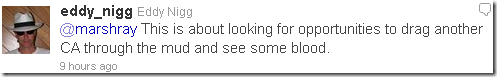
But isn’t he himself that wants to argue with everybody instead of sorting things out?
The silly challenge to Ivan Ristic:
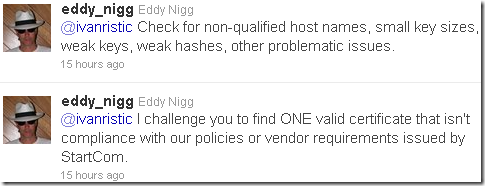
According to his CSP [4], a sort of a weird statement is made regarding security, basically provides no assurances for customers, just for Nigg himslef:
"The certification services are operated according to the highest possible levels of security and to the highest industry standards, but without any warranty."
And about the challenge itself, he mentions “weak keys”. A key can be weak in many ways.
For example, when generating a CSR and the needed RSA keys pair, easily one can end up with weak keys when it does not provide enough entropy to generate strong keys. It can even create a tool that does that on purpose and make it public.
I sincerely doubt that StartSSL or any other CA won’t sign these CSRs; it’s not all about the Debian issue.
Does he claim that his CA only signs CSRs whose corresponding RSA keys are at full strength ?
And the threats made to Ivan Ristic won’t even worth a mention in here.
Also, a vendor should not tell a customer to mind his own business, a little diplomacy instead of arrogance can go a long way.
References
[1] Web authentication authority suffers security breach
http://www.theregister.co.uk/2011/06/21/startssl_security_breach/
[2] Eddy Nigg’s Twitter page
http://twitter.com/#!/eddy_nigg
[3] Apple Root Certificate Program
http://www.apple.com/certificateauthority/ca_program.html
[4] StartSSL CA Policy & Practice Statements
http://www.startssl.com/policy.pdf