|
17.08.2008
VPN-Q 2006 Enterprise Edition Logging Capabilities
- 1. Logging on ISA
- 2. Logging on the VPN Client
1. Logging on ISA
Obviously we need a central logging mechanism on ISA to be able to see if the remote users maintain the health of their machines and what was the status of the checks performed by VPN-Q 2006 on their machines.
VPN-Q 2006 Enterprise Edition provides such a mechanism, and logs successful releases from quarantine, or unsuccessful ones.
We can set the logging level from the VPN-Q 2006 Server Administrator, Advanced tab, see Figure1.
As you can notice, the recommended level is to log information, errors, warnings and success.
We can see the logs in Event Viewer, System.
If desired, the network admin can use these logs to build a profile for a certain user, to see if this user takes security into serious, respects the company's policies and takes good care of the health of his or her machine.
People who understand and respect the security policies of the company can be rewarded, and against the hapless ones the management can take actions.
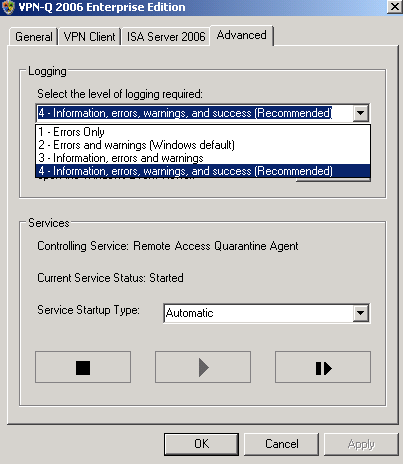
Figure1: VPN-Q 2006 Admistrator - Advanced Tab: Logging Level
In Figure2 we can spot that the user adrian was successfully released from quarantine. There is a lot of useful info in this log, we can look at the status of every security check performed on the VPN client.
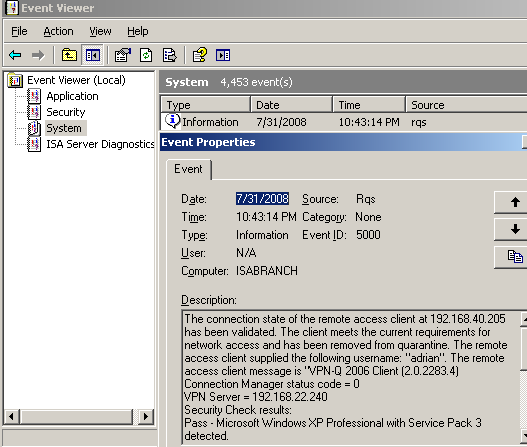
Figure2: Event Viewer - RQS: Client Successfully Released From Quarantine
An unsuccessful release from quarantine can be seen in Figure3 and Figure4.
This time the user adrian failed some security checks, IP routing is enabled and the antivirus definitions are out of date.
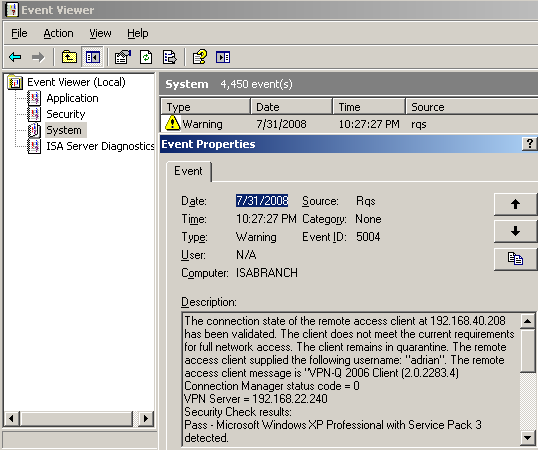
Figure3: Event Viewer - RQS: Client Does Not Meet The Current Requirements For Full Network Access
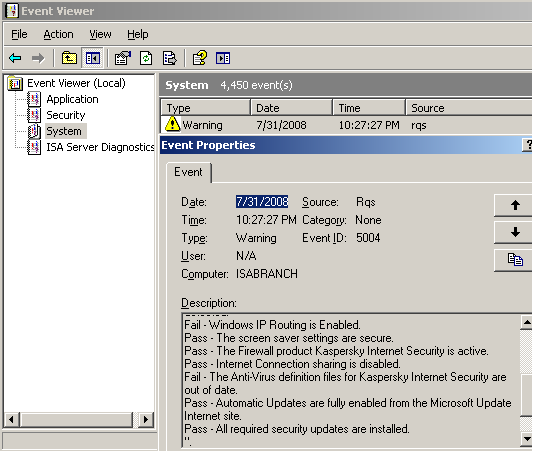
Figure4: Event Viewer - RQS: Client Does Not Meet The Current Requirements For Full Network Access, Fail Details
If you are using certificates for IKE authentication for L2TP/IPsec VPN connections, and a client fails the security checks, see Figure5, then, if you look into the Security events, you will indentify the machine which was used by the VPN client. For example, the VPN client adrian used a domain member machine called winxp.carbonwind.net(I've issue to it a computer certificate, thus the CN on that certificate will be the FQDN of the machine), see Figure6. An interesting aspect with L2TP/IPsec, is the fact since we have two distinct levels of authentication(machine and user), and the certificate used for machine authentication is stored on the machine, you can prevent the users to use unauthorized machines for VPN connections, and also, since unique certificates are issued for every machine, you can identify the origins of the IKE authentication.
So you know that user adrian is supposed to have used the machine that had installed a specific certificate.
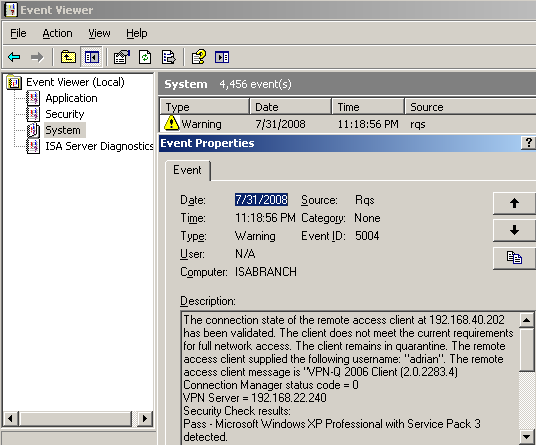
Figure5: Event Viewer - RQS: Client Does Not Meet The Current Requirements For Full Network Access
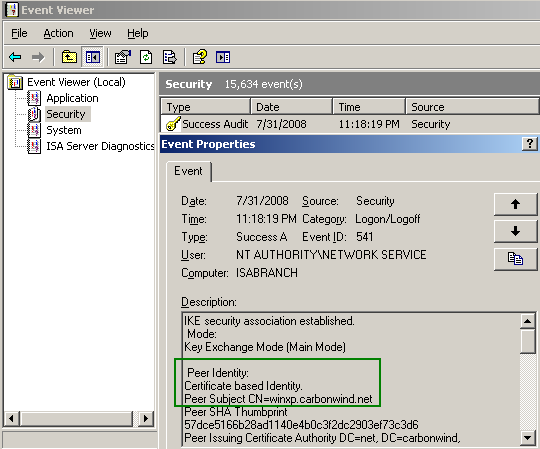
Figure6: Event Viewer - Security Audit: IKE Authentication With Certificates
The event from Figure7 was logged in case of a successful release from quarantine for a user who had used EAP-TLS for user authentication. The user name that appears in this log is the Principal Name from the SAN field of the user's certificate, see Figure8.
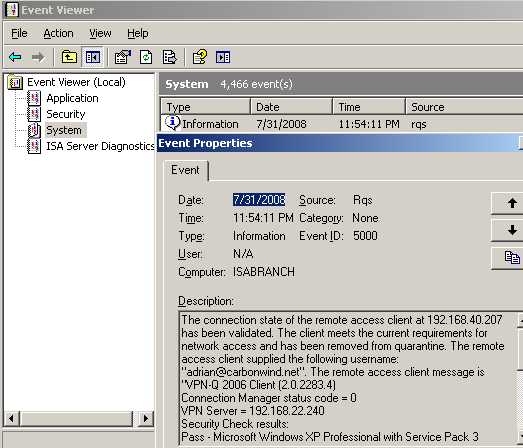
Figure7: Event Viewer - RQS: Logged Event For a Client who Used EAP-TLS for User Authentication
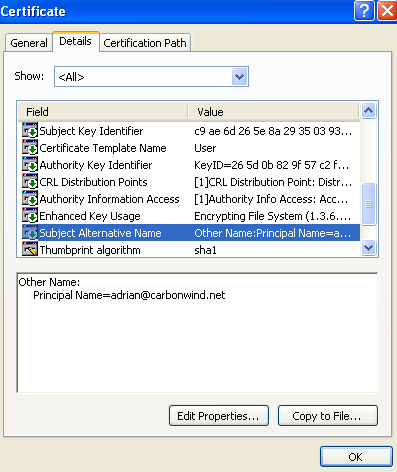
Figure8: User Certificate - SAN: Principal Name
If you want to find out more about the PPP authentication, you can check the PPP log on ISA, see Figure9. Note that you need to enable it from the RRAS console(see this Microsoft doc about PPP logging).
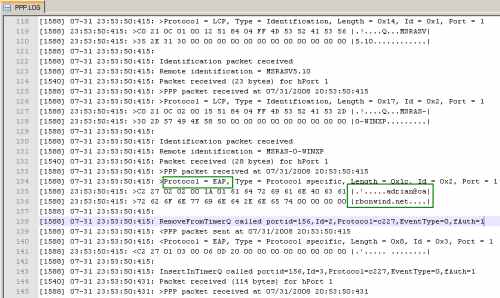
Figure9: ISA - PPP Log: EAP
2. Logging on the VPN Client
You can right-click the installed CMAK profile on the user's machine, and then click View Log, see Figure10.
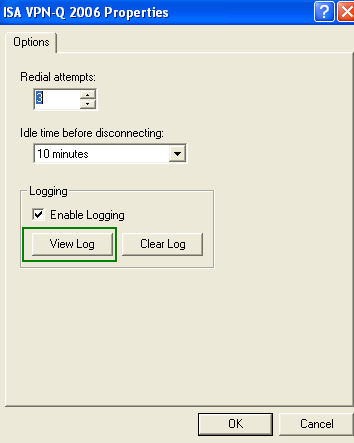
Figure10: ISA VPN-Q 2006 CMAK Profile - View Log
Within the log window that appear, you can check if the custom actions were executed correctly, if the VPNQC.exe program was successfully launched, see Figure11.
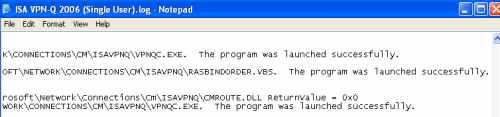
Figure11: VPN-Q 2006 Client - User Log
Although not a logging mechanism, the VPN-Q 2006 Client displays on the client the status of the security checks performed, so in case the client does not pass some security checks, he or she knows what check failed, see Figure12.
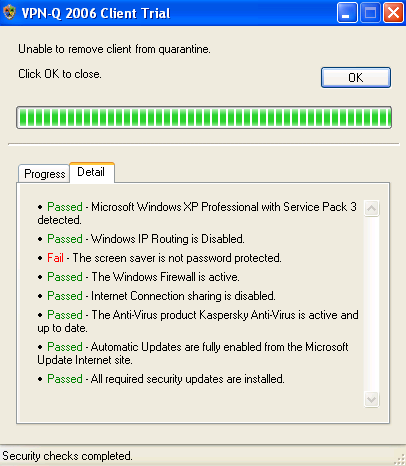
Figure12: VPN-Q 2006 Client - Detail Tab
|