|
01.06.2008
Running TMG (Threat Management Gateway) in Hyper-V
I was thinking for quite a while now to run a second OS on my laptop, and to keep it "clean" for virtualization purposes.
The shiny Windows Server 2008 x64 looks like a nice choice to me.
So I've installed for testing and evaluation Windows Server 2008 x64 Standard as my second OS on my laptop.
And decided to use Hyper-V instead of VMware Server or VMware Workstation.
Hyper-V appears a pretty slick and easy to use product, however, currently I'm not totally convinced to use Hyper-V on my laptop instead of VMware products.
For me the main drawbacks, at this moment, are:
- lack of USB support
- unsure of what/how many OS' are supported.
The VMware products look more mature and flexible.
But I kinda like Hyper-V and I plan to use it for some time from now.
You may want to read the Hyper-V FAQ.
You may also like to read these interesting presentations:
- BH07_Baker_WSV_Hypervisor_Achitecture.pdf
- BH07_Baker_WSV_Hypervisor_Security.pdf
I was playing with TMG Beta 1 in VMware Workstation 6.
Now that I had the chance, I decided to spin the wheel a little bit in Hyper-V.
It was not quite a walk in the park, although it can be, if you know what you are doing.
I've managed somehow to nail it a couple of times (including to blue-screen two different TMG VMs).
Don't get my wrong, you can get TMG Beta 1 up and running in Hyper-V from the first try.
Actually I would dare to say that after the RC1 update for the Hyper-V role, I've enjoyed a better experience with TMG Beta 1 in Hyper-V compared with TMG Beta 1 in VMware Workstation 6 on my laptop.
About the update:
- http://support.microsoft.com/kb/950049
- Windows Virtualization Team Blog : Hyper-V RC1 Release Available on Microsoft Download Center!
I did not use at the beginning the updated Hyper-V role.
If you want to learn how to add the Hyper-V role, please read Tarek Majdalani's article:
- Installing Hyper-V and Deploying Windows Server 2008 as Your First Virtual Machine - Part I
I was thinking to start with a simple lab, two VMs:
- a VM on which to install Windows Server 2008 x64 Enterprise Edition for the DC of this lab.
- a VM on which to install Windows Server 2008 x64 Standard Edition for TMG Beta 1.
First thing I've run into was the fact that I can't use "directly" my wireless adapter in Hyper-V.
For allowing Internet connectivity for the TMG VM, I need to bind this VM to my wireless adapter.
Fortunetely there is a simple solution to this problem, you may like to read John Paul Cook's article:
- Using Wireless with Hyper-V
I've added an "Internal only" Virtual Network (called ForBridgeVN), and bridged the virtual network adapter and my wireless adapter, see Figure1 and Figure2 .
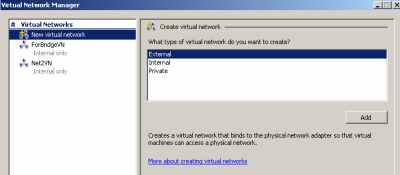
Figure1: Hyper-V: Virtual Networks
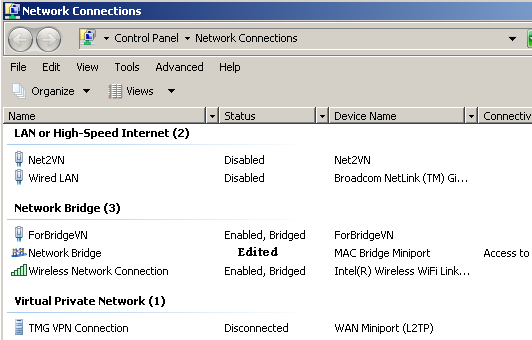
Figure2: Network Adapters on the Host
Note that the Windows Firewall is enabled on the Network Bridge, see Figure3. This does not prevent me to establish, for example a VPN connection to the TMG from my host OS or to access a web server published through TMG.
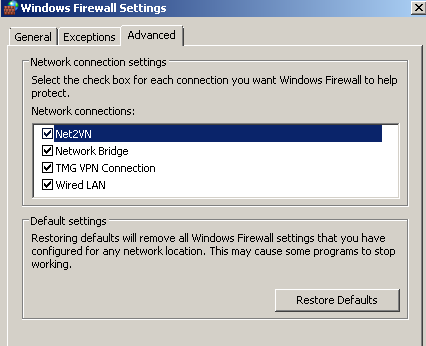
Figure3: Windows Firewall Settings
I've created a VM on which to install Windows Server 2008 x64 Enterprise Edition for the DC of this lab.
I've used a Network Adapter for it and the "Net2VN" virtual network, see Figure4.
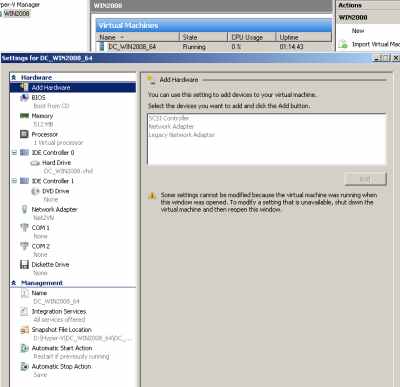
Figure4: Hyper-V: DC VM Settings
And installed Windows Server 2008 x64 Enterprise Edition on it and configured it as a DC. No major problems here, see Figure5.
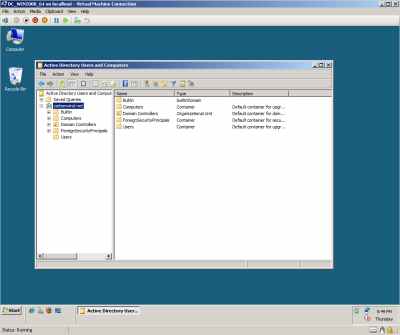
Figure5: Hyper-V: My DC VM up and running
Then I've created a VM on which to install Windows Server 2008 x64 Standard Edition for the TMG Beta 1.
I've used two Network Adapters for it: "ForBridgeVN" and "Net2VN" virtual networks. Syntethic NICs, see Figure6.
If you want to find out more about Hyper-V terminology, please read Ben Armstrong's article: Hyper-V Terminology.
Figure6: Hyper-V: TMG VM Network Adapters - Syntethic
And ran into troubles because of the synthetic NICs on TMG.
The installation of Windows Server 2008 x64 Standard Edition completed without problems.
When I've started the DC VM and attempted to start the TMG VM in order to make it a domain member, I've received an error, see Figure7.
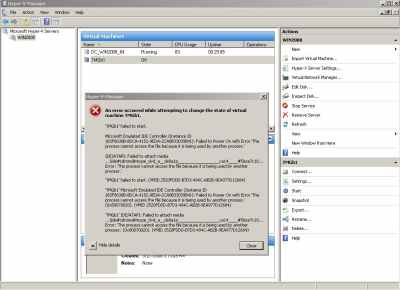
Figure7: Hyper-V: "DVD Error"
Looking at the error I've noticed something about the dvd word.
Both VMs were configured to use my physical DVD drive, see Figure8.
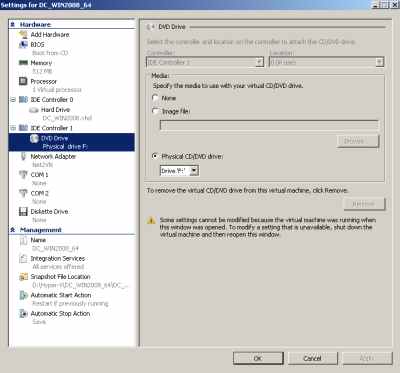
Figure8: Hyper-V: DC VM - CD/DVD Drive
I've simply checked None in the Specify the media to use with your virtual CD/DVD drive on the TMG VM.
And after that the VM started with no problems.
Made it a domain member, no issues with that either.
Then went and installed TMG on it.
If you want to learn how to install TMG Beta 1 and create a web accesss policy, check doctor Tom Shinder's guides:
- Installing the Forefront Threat Management Gateway (Forefront TMG) Beta 1
- Creating a Web Access Policy using the Forefront Threat Management Gateway (TMG) Beta 1 (Part 1)
Don't forget about configuring the update settings on the TMG, see the bellow Technet document:
http://technet.microsoft.com/en-us/library/cc441562.aspx
Actually the istallation succeeded.
But I had connectivity problems. "Ping" was fine (ping tests are pretty much meaningless, there is no proof that things are actually working), however I've lost the "domain connectivity" and I could not pass traffic through the TMG.
Looking at the Alerts tab, I've noticed a couple of alerts (one of them was telling me something about connectivity to the DC).
Unfortunetely I did not take any printscreens at that time, so no pictures.
Messed a little bit with a couple of settings and then I've decided to start with a fresh VM.
Same issues.
And I've rebuilt one more time the TMG VM (I like to keep things clean), this time using Legacy Network Adapters, see Figure9.
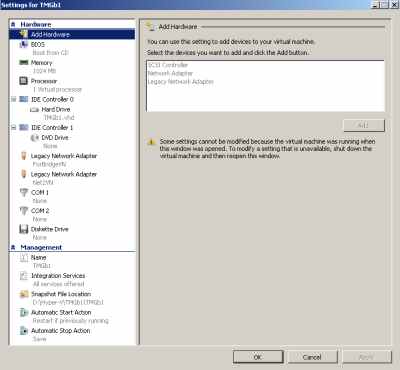
Figure9: Hyper-V: TMG VM Legacy Network Adapters - Emulated
And success: the beast was up and running, looking happy, see Figure10.
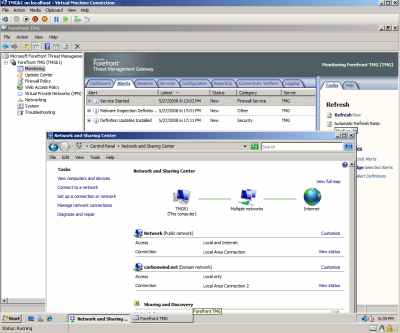
Figure10: Hyper-V: TMG up and running
Then I've decided to install the Hyper-V update, see Figure11.
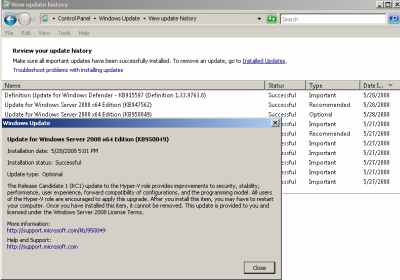
Figure11: Hyper-V: RC1 Update
And I could not start my VMs anymore, see Figure12. Note that in Figure12 I've already "fixed" the DC VM.
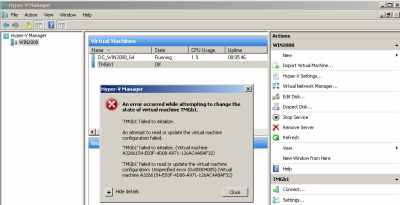
Figure12: Hyper-V: Failed to Start VM After Update
I did not waste too much time troubleshooting this.
I've created two new VMs (for DC and TMG), and used for them the virtual HDDs from my previous VMs, see Figure13.
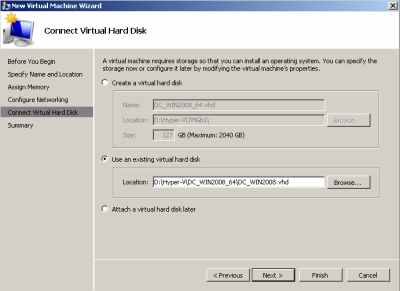
Figure13: Hyper-V: Using the Old Virtual HDD
- On the DC VM, I needed to update the drivers, the NIC was no longer detected, see Figure14 and Figure15. No problems, configured the new NIC with the required IP settings and things looked good.
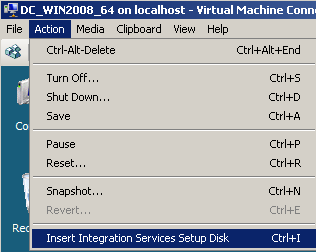
Figure14: Hyper-V: DC VM - Insert Integration Services Setup Disk
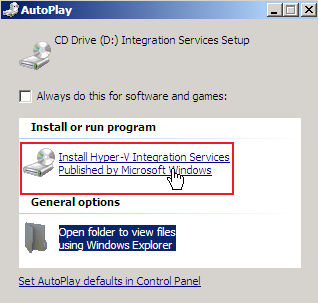
Figure15: Hyper-V: DC VM - Install Hyper-V Integration Services
- On the new TMG machine I've used again "Legacy Network Adapters". And one more time the beast was up and running, looking happy.
Actually Hyper-V seems faster now, I have no scientific data to back my comments (I did not do any tests), I just "feel" that some performance was gained, at least on my laptop.
Anyway, I've decided to start with a fresh lab after the update (the new DC VM is called now DC_WINx64, I've kept the old name for the TMG VM).
Now I've used the "working settings" and everything went smoothly.
I did a quick test to see that the malware inspection was running using the EICAR test file. I have the following firewall policies on the TMG, see Figure16.
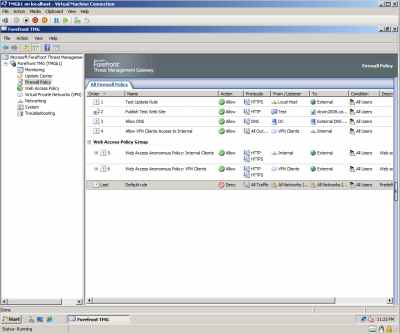
Figure16: Hyper-V: TMG Beta 1 - Firewall Policies
And the download of the EICAR test file was blocked by TMG, see Figure17 and Figure18.
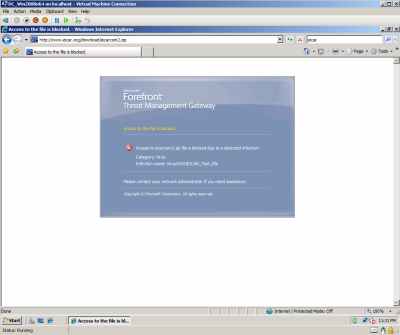
Figure17: Hyper-V: Host Behind TMG Beta 1 - The Download of Infected File Was Blocked by TMG
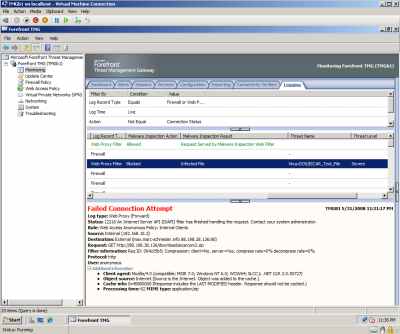
Figure18: Hyper-V: TMG Beta 1 Log - The Download of Infected File Was Blocked
I wanted to test inbound connectivity too. As can be noted from Figure16 , I have used a web server publishing rule to publish a web server behind TMG (it's actually an IIS7 web server running on the DC VM, I'm not worried about security issues, I'm in my private lab and this is just a test).
I can access a web server located behind TMG with no problems from my host OS, see Figure19. Note that I did not modified the firewall settings on the host machine, see Figure20.
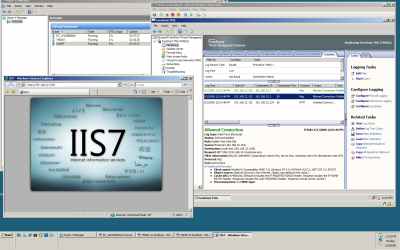
Figure19: Hyper-V: Access From the Host OS a Web Server Located Behind TMG Beta 1
Figure20: Host Windows Firewall Settings
As can be seen in Figure19, I've added another VM, running Windows XP x32 SP3. Its settings are shown in Figure21. Note that I can use a Network Adapter because I had applied SP3, on SP2 I cannot install the Hyper-V Integration Services.
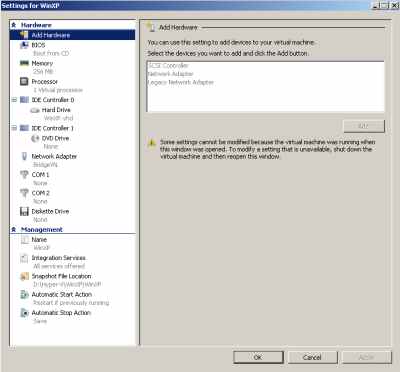
Figure21: Hyper-V: Windows XP SP3 VM Settings
I can access from it the web server located behind TMG with no problems too, see Figure22 and Figure23.
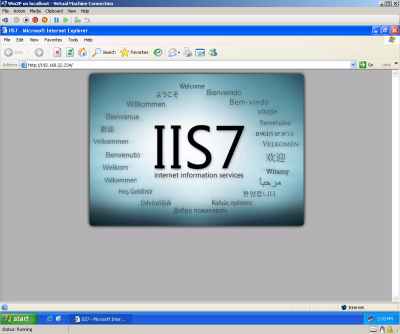
Figure22: Hyper-V: Windows XP SP3 VM - Accessing The Web Server Located Behind TMG Beta 1
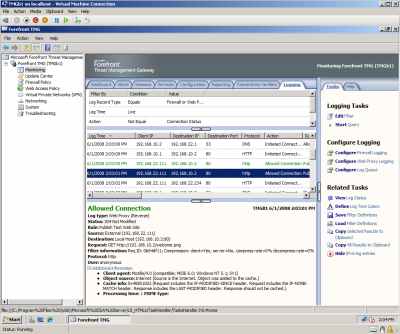
Figure23: Hyper-V: TMG Beta 1 Log
I also wanted to test if I can establish a VPN connection(L2TP/IPsec) from the WinXP VM. No problems, see Figure24, Figure25 and Figure26.
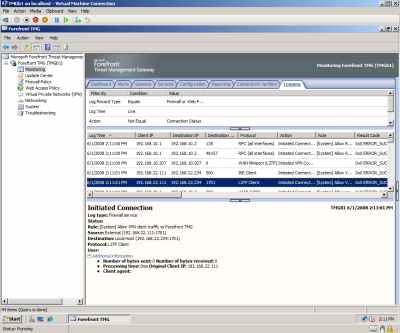
Figure24: Hyper-V: TMG Beta 1 - VPN Connection Log
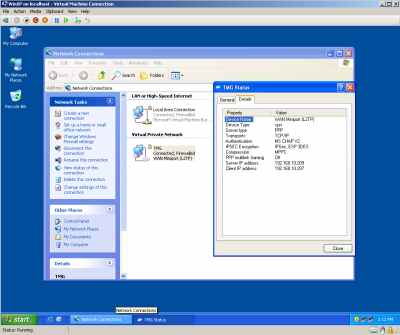
Figure25: Hyper-V: WinXP VM: VPN Connected
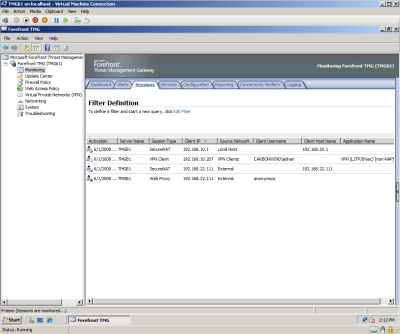
Figure26: Hyper-V: TMG Beta 1 - VPN Sessions
As it should be, split-tunneling is disabled on the WinXP VM, and I'm accessing Internet through the TMG over the VPN connection, see Figure27 and Figure28.

Figure27: Hyper-V: WinXP SP3 VM: Internet Access Over the VPN Connection
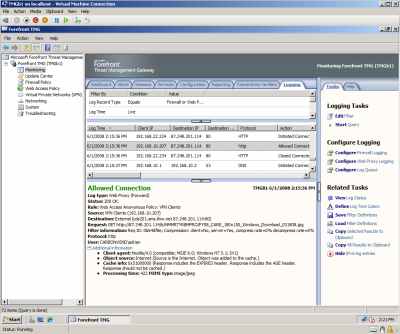
Figure28: Hyper-V: TMG Beta 1 - VPN Connection Log
And since I've specified on my access rule which allows Internet Access to VPN Clients that Malware Inspection to be applied, I've tested it:
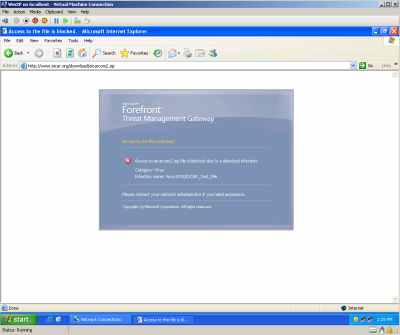
Figure29: Hyper-V: WinXP VM - The Download of the Infected File Over the VPN Connection Was Blocked
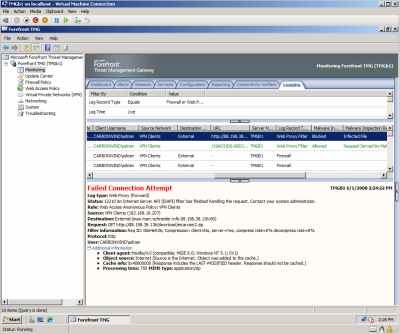
Figure30: Hyper-V: TMG Beta 1 - The Download of Infected File Was Blocked Over the VPN Connection Was Blocked
Searching a little bit, I found this interesting post from Jim Harrison:
http://www.freelists.org/archives/isapros/05-2008/msg00059.html
Thus I've decided to try one more time with Network Adapters on the TMG VM, now that I've updated to Hyper-V RC1.
So I've started from zero, a fresh lab.
New Virtual Networks on Hyper-V, see Figure31.
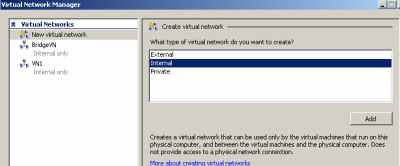
Figure31: Hyper-V: New Virtual Networks
The new NICs on the host can be seen in Figure32.
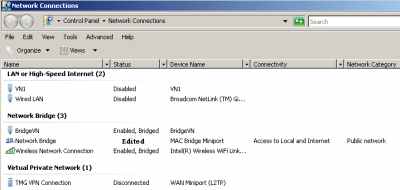
Figure32: New NICs on the Host
The settings for the new DC VM are shown in Figure33.
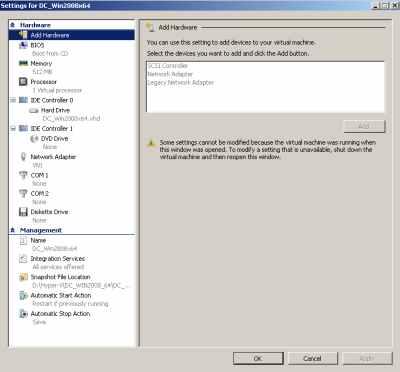
Figure33: New DC VM Settings
The settings for the new TMG VM are shown in Figure34.
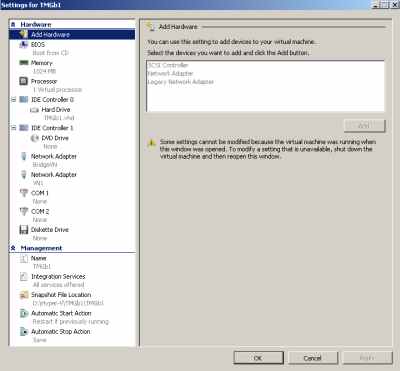
Figure34: New TMG VM Settings
And installed TMG.
Like before installation succeeded, but now something has changed.
"Ping" connectivity is fine and apparently I do have "domain connectivity" and also some Internet connectivity on the TMG, see Figure35 and Figure36. A weird thing is the fact that the order of the NICs on the TMG VM does not appear to be correct ("LAN Area Connection" should be the Internet facing NIC, see Figure34), but this was like so before I've installed TMG (every time I'm using Network Adapters).
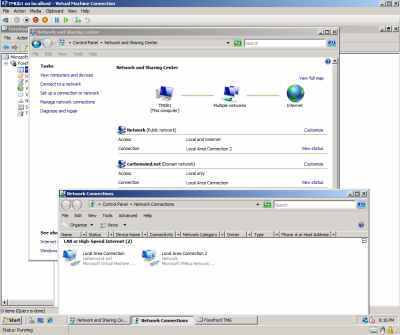
Figure35: Hyper-V: TMG VM - Synthetic NICs
Figure36: Hyper-V: TMG Beta 1 VM - Add Users
However I'm not able to pass traffic through the TMG, or actually only sometimes/sporadically traffic passes through TMG.
And I cannot update the TMG machine, see Figure37.
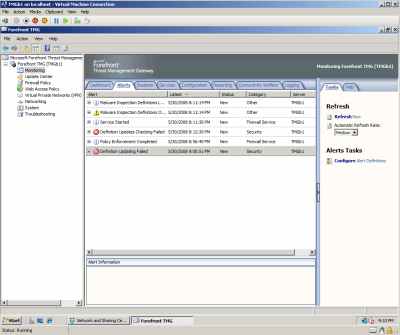
Figure37: Hyper-V: TMG Beta 1 VM - Alerts
So it still does not work for me with Network Adapters after the Hyper-V update to RC1.
If I go and remove the Network Adapters on this VM and instead add Legacy Network Adapters (see Figure38), things immediately start to work, see Figure39 (now the order of the NICs on the TMG VM is correct).
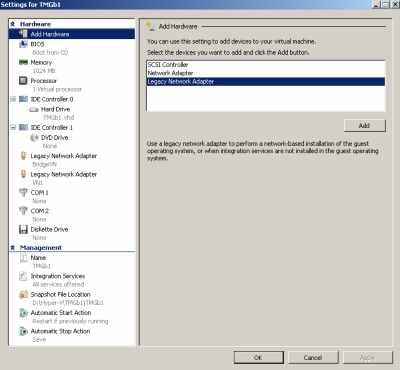
Figure38: Hyper-V: TMG VM - Changed to Emulated NICs
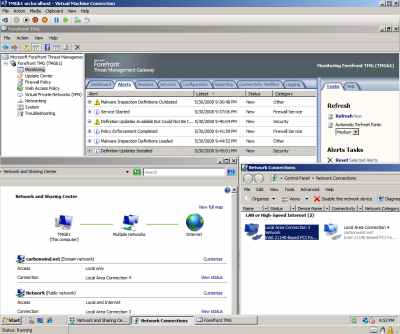
Figure39: Hyper-V: TMG Beta 1 VM - up and running
So currently I'm using TMG with Legacy Network Adapters in Hyper-V RC1.
I've kept my lab this Sunday up for more than 7 hours (it's running on my laptop as my second OS, and I cannot keep it up too much right now), see Figure40, and I did not encounter any major issues.
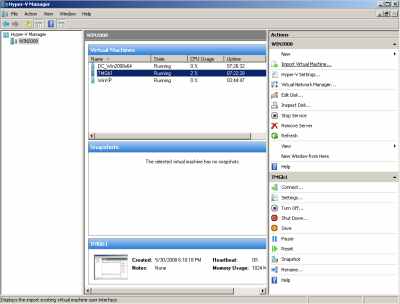
Figure40: Hyper-V: Lab Uptime
|