|
29.09.2009
Fun with Forefront TMG Beta 3 and blocking download of certain file types over HTTP based on the server's response body: Part 2
- 1. RAR archives
- 2. '.mp3' audio files
- 3. '.pdf' files
- 4. Flash content
- 4.1. '.flv' files (Flash video)
- 4.2 '.swf' files (ShockWave Flash)
- 4.3 '.cws' files (FWS files compressed with ZLIB)
- 5. 7-Zip archives
- 6. GZIP archives
- 7. BZip2 archives
- 8. ZIP archives
- 9. '.msi' and '.msp' files
- 10. Windows Executable Content
- 11. A few words
The bellow document, File Signatures Table, written by Gary C. Kessler, might help you with TMG's HTTP filter signatures:
http://www.garykessler.net/library/file_sigs.html
1. RAR archives
Say you want to block responses containing RAR archives(note that we won't cover now the Windows self-extracting RAR archives).
A quick Google search about RAR files format and we may find this:
http://www.win-rar.com/index.php?id=24&kb=1&kb_article_id=162
Let's open a RAR archive within a hex editor, see Figure17:
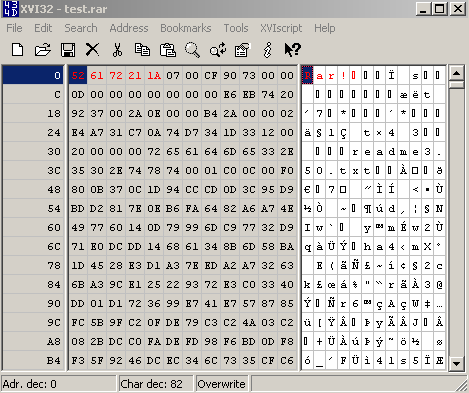
Figure17: RAR Archive - Hex View
As can be noted from Figure17, I've already marked(with red color) some bytes. We need to instruct TMG Beta 3 to block this string in the web server's response.
Figure18 and Figure19 shows us a possible signature to block responses containing RAR archives. As can be seen from Figure18 I've limited the byte range, as we usually search a few "start bytes".
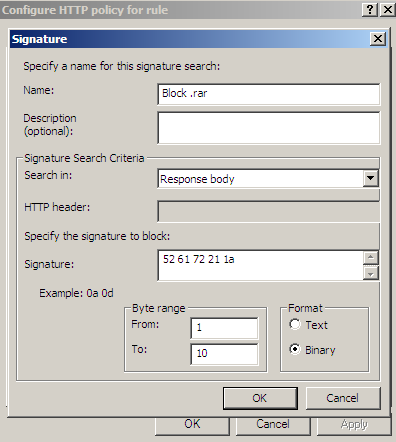
Figure18: Forefront TMG Beta 3 - Block responses containing RAR archives by hex signature
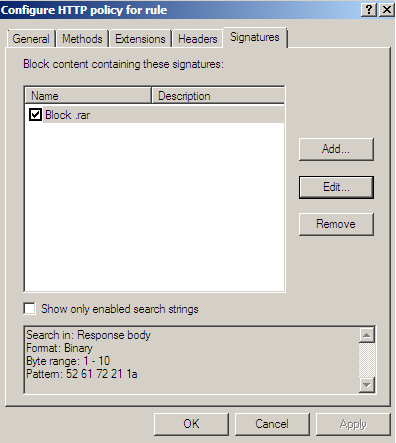
Figure19: Forefront TMG Beta 3 - Enabled signatures
And now, if I simply change the extension of a '.rar' file to a '.jpg' one and attempt to download it, Forefront TMG Beta 3 should block this cheap trick, see Figure20:
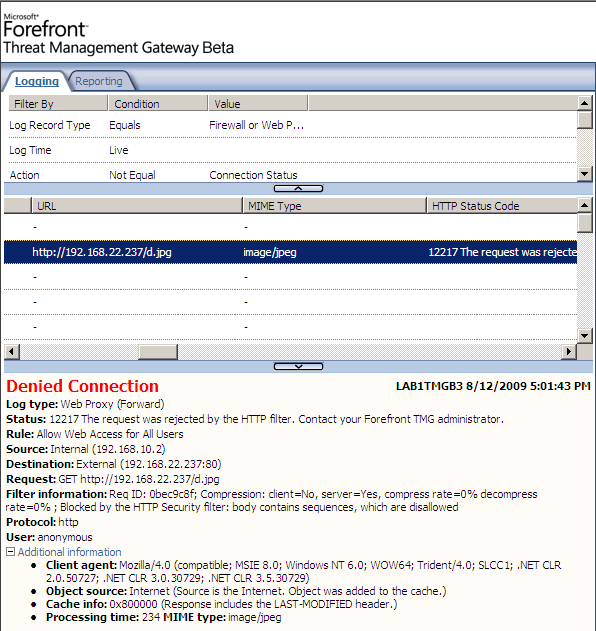
Figure20: Forefront TMG Beta 3 - Blocked "masked" RAR archive
2. '.mp3' audio files
Say you want to block responses containing '.mp3' audio files.
A quick Google search about '.mp3' files format and we may find this:
http://en.wikipedia.org/wiki/ID3
Let's open a '.mp3' file within a hex editor, see Figure21:
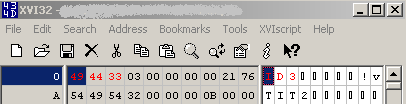
Figure21: '.mp3' file - Hex View
As can be noted from Figure21, I've already marked(with red color) some bytes. We need to instruct TMG Beta 3 to block this string in the web server's response.
Figure22 shows us a possible signature to block responses containing '.mp3' files. As can be seen from Figure22 I've limited the byte range, as we usually search a few "start bytes".
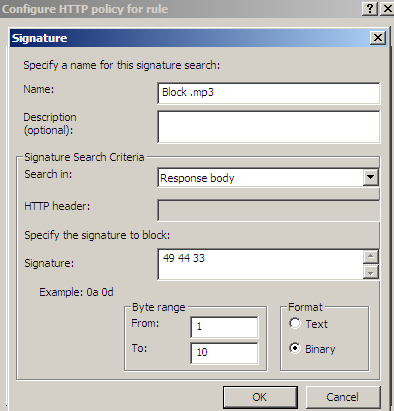
Figure22: Forefront TMG Beta 3 - Block responses containing '.mp3' audio files by hex signature
3. '.pdf' files
Say you want to block responses containing '.pdf' files.
A quick Google search about '.pdf' files format and we may find this:
http://blogs.adobe.com/insidepdf/Compatibility_090819.pdf
Let's open a '.pdf' file within a hex editor, see Figure23:
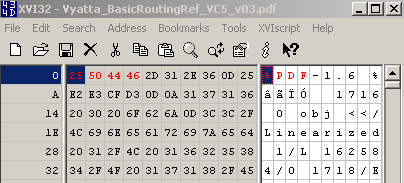
Figure23: '.pdf' file - Hex View
As can be noted from Figure23, I've already marked(with red color) some bytes. We need to instruct TMG Beta 3 to block this string in the web server's response.
Figure24 shows us a possible signature to block responses containing '.pdf' files. As can be seen from Figure24 I've limited the byte range, as we usually search a few "start bytes".
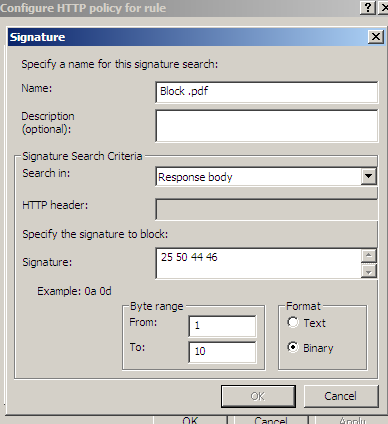
Figure24: Forefront TMG Beta 3 - Block responses containing '.pdf' files by hex signature
4. Flash content
This could be an interesting one, giving the recent Adobe Flash Player security flaws.
You can have a chance of blocking flash content at the gateway, if flash is not needed for your business.
By flash content we may understand the following:
- 4.1 '.flv' files (Flash video)
- 6. '.swf' files (ShockWave Flash)
- 7. '.cws' files (FWS files compressed with ZLIB)
4.1 '.flv' files (Flash video)
Say you want to block responses containing '.flv' files.
A quick Google search about '.flv' files format and we may find these:
http://www.adobepress.com/articles/article.asp?p=1014968
http://en.wikipedia.org/wiki/Flash_Video
http://www.digitalpreservation.gov/formats/fdd/fdd000130.shtml
http://osflash.org/flv
Let's open a '.flv' file within a hex editor, see Figure25:
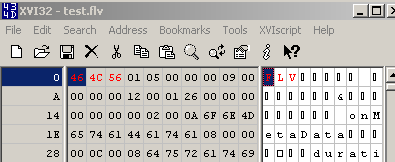
Figure25: '.flv' file - Hex View
As can be noted from Figure25, I've already marked(with red color) some bytes. We need to instruct TMG Beta 3 to block this string in the web server's response.
Figure26 shows us a possible signature to block responses containing '.flv' files. As can be seen from Figure26 I've limited the byte range, as we usually search a few "start bytes".
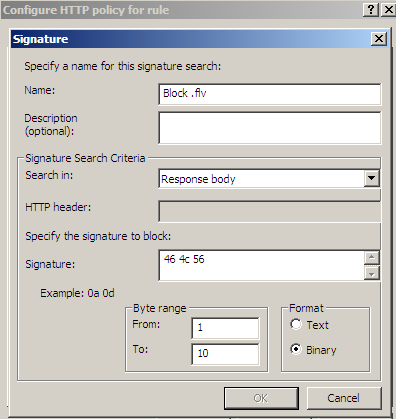
Figure26: Forefront TMG Beta 3 - Block responses containing '.flv' files by hex signature
4.2 '.swf' files (ShockWave Flash)
Say you want to block responses containing '.swf' files.
A quick Google search about '.swf' files format and we may find these:
http://www.adobepress.com/articles/article.asp?p=1014968
http://en.wikipedia.org/wiki/Adobe_Flash
http://www.half-serious.com/swf/format/
http://www.digitalpreservation.gov/formats/fdd/fdd000130.shtml
Let's open a '.swf' file within a hex editor, see Figure27:
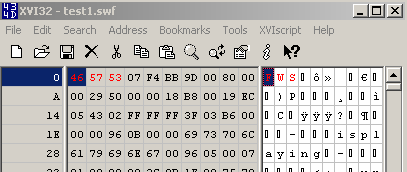
Figure27: '.swf' file - Hex View
As can be noted from Figure27, I've already marked(with red color) some bytes. We need to instruct TMG Beta 3 to block this string in the web server's response.
Figure28 shows us a possible signature to block responses containing '.swf 'files. As can be seen from Figure28 I've limited the byte range, as we usually search a few "start bytes".
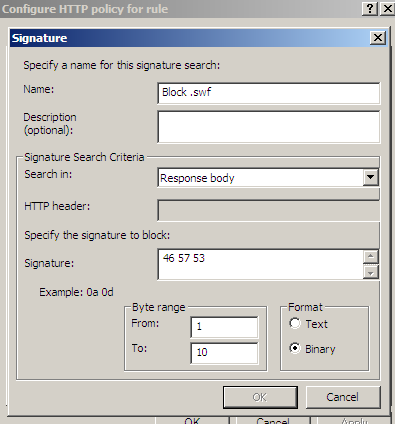
Figure28: Forefront TMG Beta 3 - Block responses containing '.swf' files by hex signature
4.3 '.cws' files (FWS files compressed with ZLIB)
Say you want to block the responses containing '.cws' files.
A quick Google search about '.cws' files format and we may find these:
http://www.digitalpreservation.gov/formats/fdd/fdd000130.shtml
http://zefonseca.com/cws2fws/
Let's open a '.cws' file within a hex editor, see Figure29:
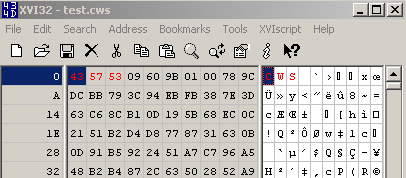
Figure29: '.cws' file - Hex View
As can be noted from Figure29, I've already marked(with red color) some bytes. We need to instruct TMG Beta 3 to block this string in the web server's response.
Figure30 shows us a possible signature to block responses containing '.cws' files. As can be seen from Figure30 I've limited the byte range, as we usually search a few "start bytes".
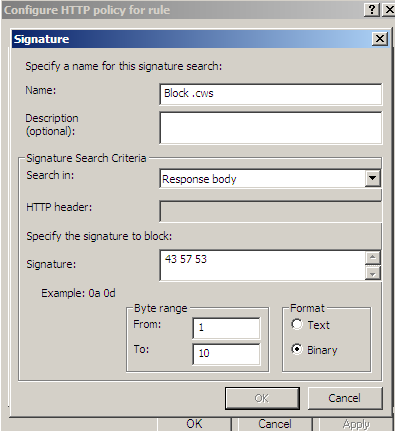
Figure30: Forefront TMG Beta 3 - Block responses containing '.cws' files by hex signature
5. 7-Zip archives
Say you want to block responses containing 7-Zip archives(note that we won't cover now the Windows self-extracting 7-Zip archives).
Let's open a 7-Zip archive within a hex editor, see Figure31:
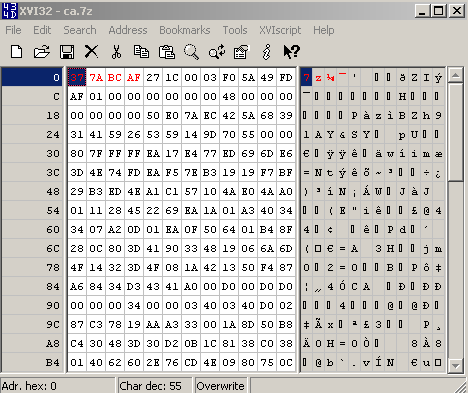
Figure31: 7-Zip Archive - Hex View
As can be noted from Figure31, I've already marked(with red color) some bytes. We need to instruct TMG Beta 3 to block this string in the web server's response.
Figure32 shows us a possible signature to block responses containing 7-Zip archives. As can be seen from Figure32 I've limited the byte range, as we usually search a few "start bytes".
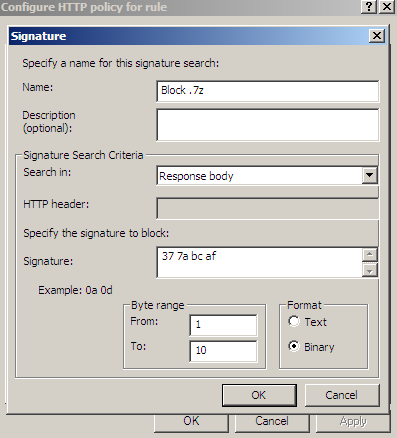
Figure32: Forefront TMG Beta 3 - Block responses containing 7-Zip by hex signature
6. GZIP archives
Say you want to block responses containing GZIP archives.
Note: The bellow signature will not block HTTP compression(using GZIP) if you configure Forefront TMG Beta 3 to request HTTP compression(I did not test with ISA Server 2006, but it shouldn't be any problems there either).
Although a GZIP compressed web server answer will contain the same beginning hex string, see Figure33, Forefront TMG Beta 3 will first decompress it, see Figure34, and then apply the HTTP inspection.
See this for more details:
http://technet.microsoft.com/en-us/library/bb794746.aspx
Where it says that:
Compression Filter. This filter is responsible for compression and decompression of HTTP requests and responses. This filter has a high priority, and is high in the ordered list of Web filters. This is because the filter is responsible for decompression. Decompression must take place before any other Web filters inspect the content.
If you do not configure Forefront TMG Beta 3 to request HTTP compression, and the web server forces HTTP compression(GZIP), this signature will block the compressed web server's response.
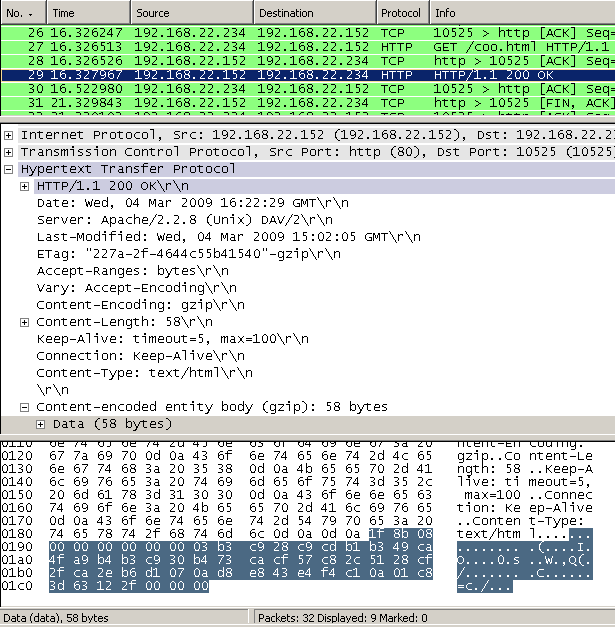
Figure33: Wireshark - Web server's answer: Compressed
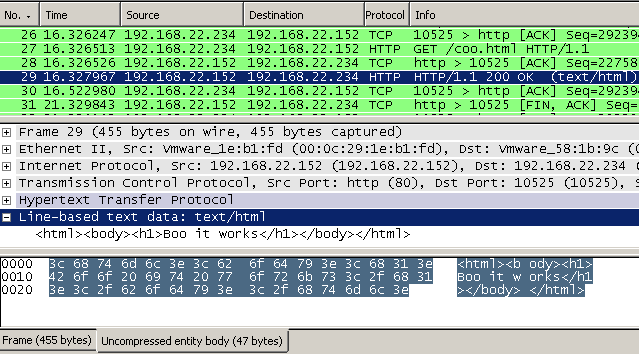
Figure34: Wireshark - Web server's answer: Decompressed
A quick Google search about GZIP files format and we may find this:
http://www.gzip.org/zlib/rfc-gzip.html
Let's open a GZIP archive within a hex editor, see Figure35:
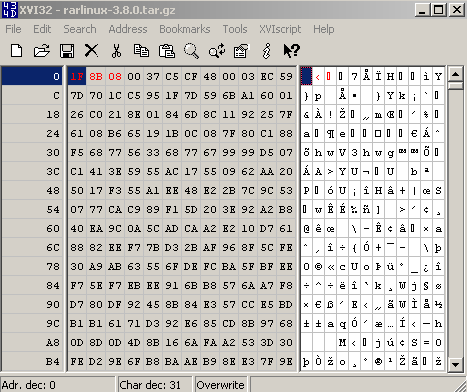
Figure35: GZIP Archive - Hex View
As can be noted from Figure35, I've already marked(with red color) some bytes. We need to instruct TMG Beta 3 to block this string in the web server's response.
Figure36 shows us a possible signature to block responses containing GZIP archives. As can be seen from Figure36 I've limited the byte range, as we usually search a few "start bytes".
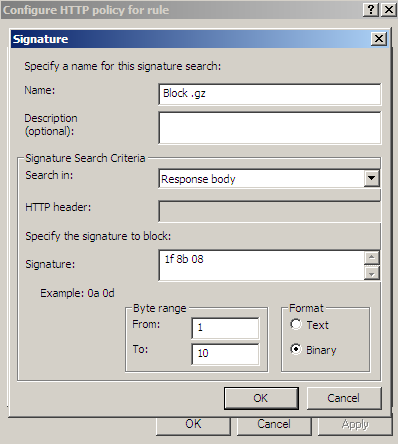
Figure36: Forefront TMG Beta 3 - Block responses containing GZIP archives by hex signature
7. BZip2 archives
Say you want to block responses containing BZip2 archives.
A quick Google search about BZip2 files format and we may find this:
http://en.wikipedia.org/wiki/Bzip2
Let's open a BZip2 archive within a hex editor, see Figure37:
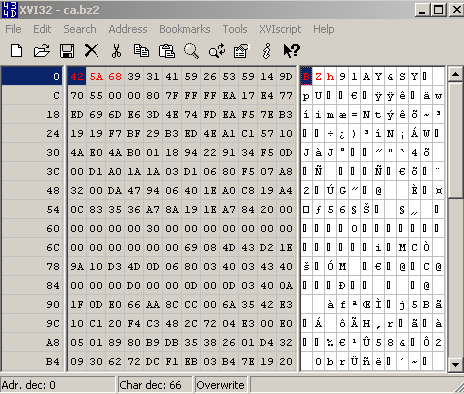
Figure37: BZip2 Archive - Hex View
As can be noted from Figure37, I've already marked(with red color) some bytes. We need to instruct TMG Beta 3 to block this string in the web server's response.
Figure38 shows us a possible signature to block responses containing BZip2 archives. As can be seen from Figure38 I've limited the byte range, as we usually search a few "start bytes".
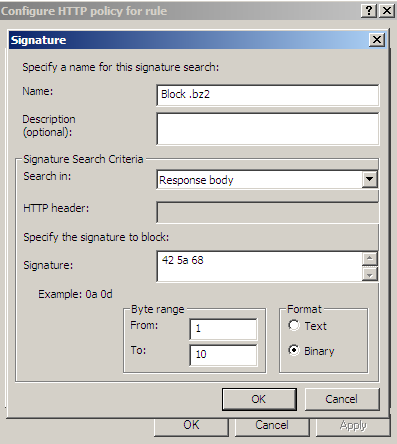
Figure38: Forefront TMG Beta 3 - Block responses containing BZip2 archives by hex signature
8. ZIP archives
Say you want to block responses containing ZIP archives(note that we won't cover now the Windows self-extracting ZIP archives).
A quick Google search about ZIP files format and we may find this:
http://www.sxlist.com/techref/language/delphi/swag/ARCHIVES0022.html
Let's open a ZIP archive within a hex editor, see Figure39:
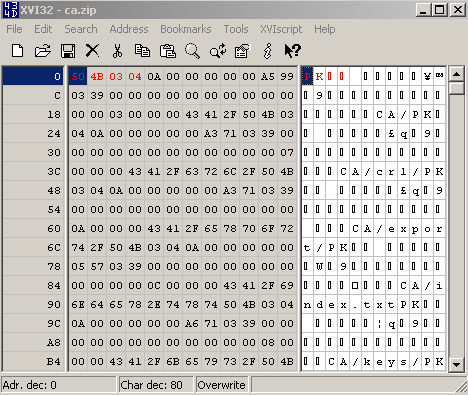
Figure39: ZIP Archive - Hex View
As can be noted from Figure39, I've already marked(with red color) some bytes.
And now the "fun" begins. The approach we've used so far will work no more. If we create a signature, see Figure40, for the marked bytes from Figure39, we will block web server responses containing other file types.
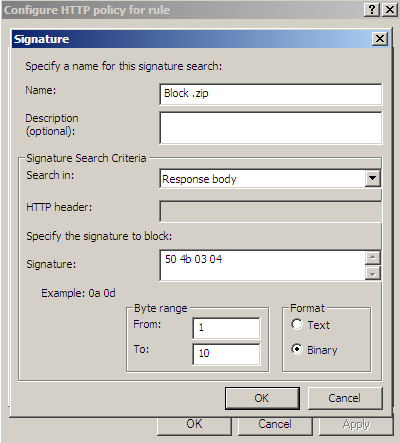
Figure40: Forefront TMG Beta 3 - Block responses containing ZIP archives by hex signature
For example, in Figure41 I've pictured some other files types which might get blocked by the above signature, say Microsoft Office '.pptx', '.docx', '.xlsx' files; or Open Office '.odt', '.ods', '.odp', '.sxw', '.sxc', '.sxi' files; or '.jar'(Java archive) files or '.xpi' files(adding Mozilla Firefox add-ons might get blocked, as TMG Beta 3 has the ability of inspecting outbound SSL traffic).

Figure41: 'PK' Multiple File Types - Hex View
If we configure Forefront TMG Beta 3 to search through more bytes, with another signature(s) we might be able to shrink down the file types to be blocked(I did not try this).
If the HTTP filter would have had the ability of constructing more advanced signatures, say using regex, we might have been able, with some extra work, to get more finesse with our signatures.
9. '.msi' and '.msp' files
Say you want to block responses containing '.msi'(Microsoft Windows Installer) and '.msp'(Windows Installer patch) files.
Let's open a '.msi' file and '.msp' file within a hex editor, see Figure42 and Figure43:
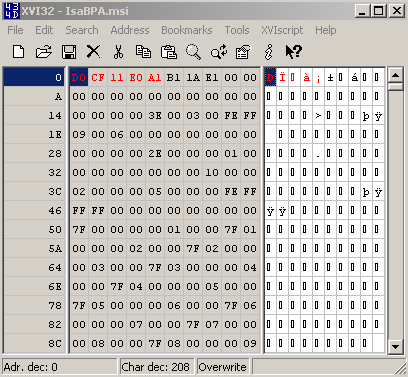
Figure42: '.msi' file - Hex View
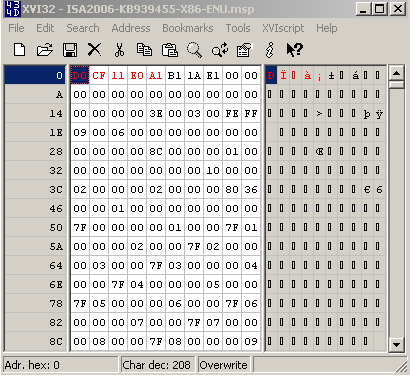
Figure43: '.msp' file - Hex View
As can be noted from Figure42 and Figure43, I've already marked(with red color) some bytes. As above with .zip archives, if we create a signature, see Figure44, for the marked bytes from Figure42 or Figure43, we will block web server responses containing other file types.
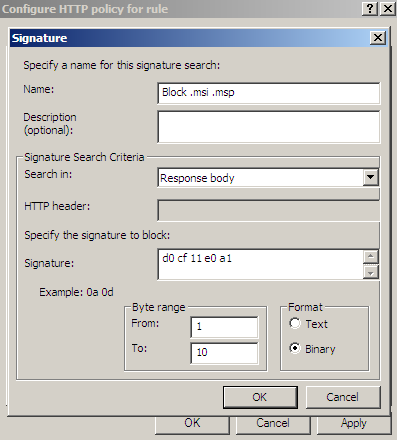
Figure44: Forefront TMG Beta 3 - Block responses containing '.msi' and '.msp' files by hex signature
For example, in Figure45 I've pictured some other files types which might get blocked by the above signature, say Microsoft Office '.ppt', '.doc', '.xls', '.vsd', '.pps' files; or Visual Studio '.suo' files.
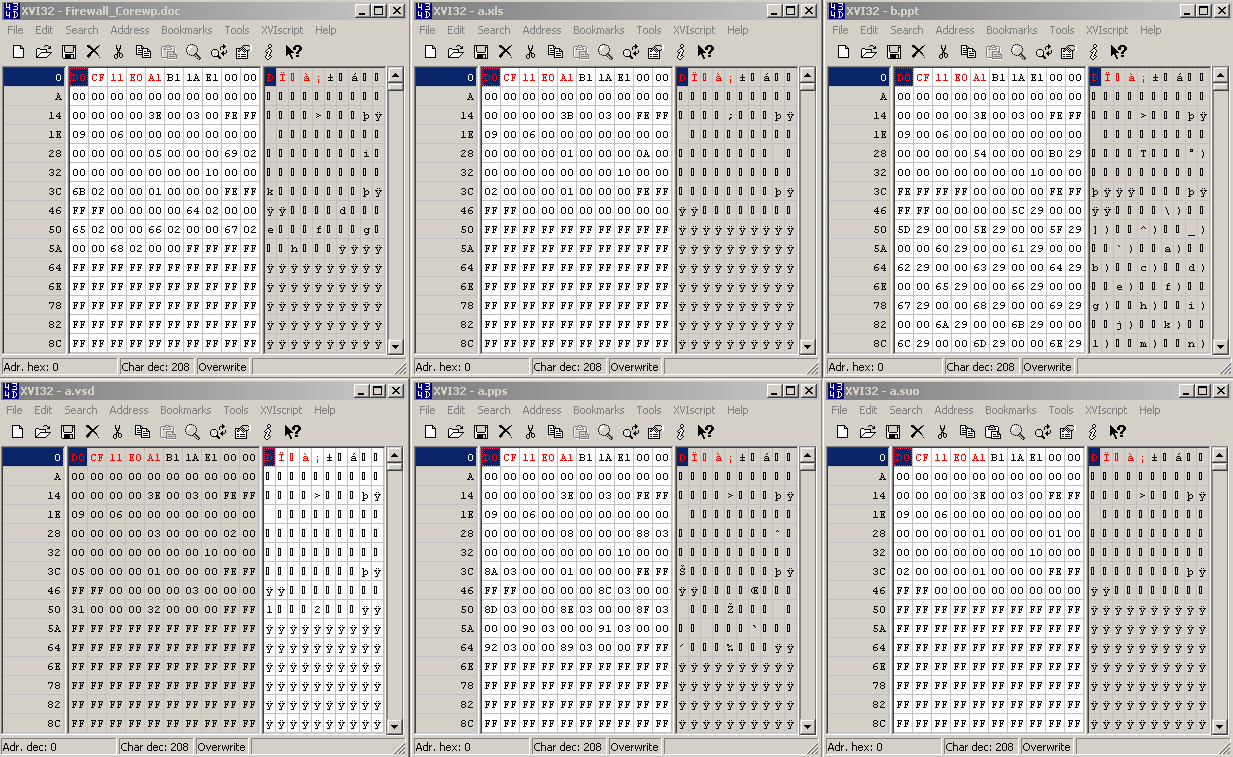
Figure45: Multiple File Types - Hex View
As with the '.zip' files, it would have been handy if the HTTP filter would have had the ability of constructing more advanced signatures, say using regex.
10. Windows Executable Content
Say you want to block responses containing Windows executable content.
As can be seen I haven't say '.exe' files. This is because bellow we will block web server's responses that begin with the 'MZ' string. And this does not mean only '.exe files', for example it means DLLs too.
Actually there is a setting on Forefront TMG Beta 3 HTTP Filter that does that, see Figure46:
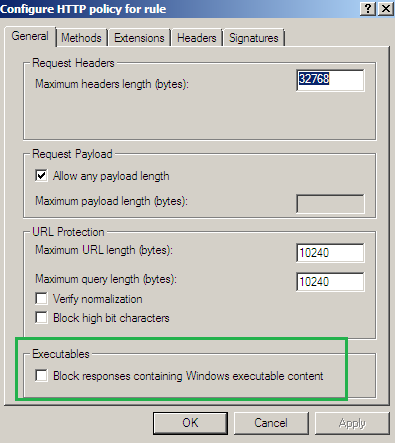
Figure46: Forefront TMG Beta 3 HTTP Filter - Block responses containing Windows executable content
Let's open an '.exe' file within a hex editor, see Figure47:
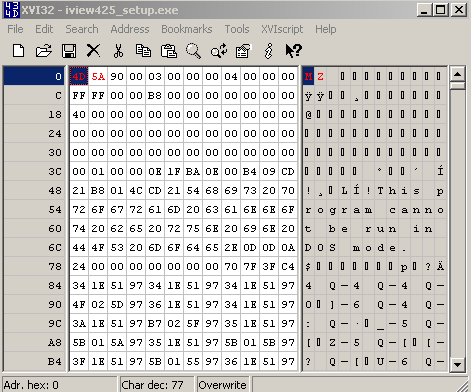
Figure35: Windows .exe file - Hex View
As can be noted from Figure47, I've already marked(with red color) some bytes.
If we create a signature, like see Figure48, for the marked bytes from Figure47, we will block web server responses containing other file types.
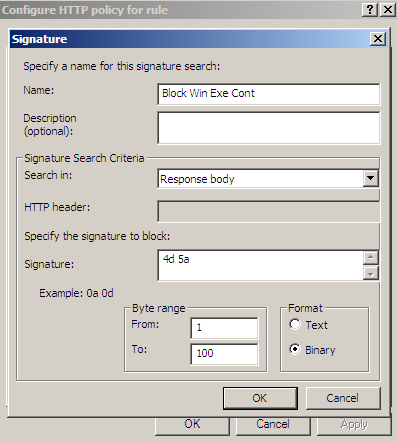
Figure48: Forefront TMG Beta 3 - Block Windows executable content by hex signature
For example, in Figure49 I've pictured some other files types which might get blocked by the above signature, say '.dll', '.scr', '.ocx', '.sys', '.ax' or '.com' files.

Figure49: 'MZ' Multiple File Types - Hex View
11. A few words
As we saw, the feature of the HTTP filter we've used above has certain limitations.
I've used Forefront TMG Beta 3 for a certain reason(remember I've mentioned this somewhere in the fist part), and this reason is the new NIS feature(IPS).
If Microsoft would allow us to create our own signatures for it, I would guess that we can come up with more complex expressions in matching certain file types based on the servers' responses.
Maybe it's not quite what Microsoft think about the NIS, but...
Also, with NIS we might put a signature just in detect mode, and log "bad" habits, as we saw from above, the logs on TMG Beta 3 do not show us what exactly disallowed sequence of characters the response contained, thus if we have multiple signatures like above, it may be a problem to tell what happended.
With a NIS signature, we will know what signature kicked in.
So let's wait and see what moves Microsoft will make in the future regarding the NIS.
|